Despite constant innovation, the nascent crypto space is swimming with hacks, scams, and attack vectors. While issues like sybil, double spending, or the 51% (majority) attacks are speared by nefarious intentions, a vampire attack is more exclusive and not exactly an immediate sabotage attempt. Instead, a vampire attack in crypto is primarily a DeFi-specific attack where one project — usually a fork of a more established name — plans to usurp the other.
From sucking liquidity and trading volume out of an existing project to luring users with better incentives, a vampire attack in crypto is a clear case of invasion. And the nature of this attack makes automated market makers and decentralized exchanges susceptible. In this guide, we explore everything to know about vampire attacks — mechanics, examples, and ways to mitigate them. Here’s what you need to know.
Unpacking vampire attacks in crypto
Vampire attacks primarily brace the DeFi space, where newer projects try to attract investors out of the more established name. As for the mechanics, each vampire attack follows a set number of steps, starting with:
Target identification
The vampire attacker starts by identifying the target, which can be an established ecosystem with high liquidity. The prerequisites to choosing the target include DEXs or AMMs with a massive user base.
Offering incentives
This is where things get interesting. The attacker, or rather the new platform, then matches the popular platform in terms of offered incentives. Some of the options for the attacker include higher yield in case the target is a liquidity provider or better staking rewards if the target is a staking service.
Launching the attack
To get the attack underway, the attacker publicizes the incentives to the target audience via marketing campaigns and direct incentives like airdrops, community outreach, and more. Once users start flocking to the new platform or rather the attacker, what ensues is a rapid liquidity shift from the target to the perpetrator. This attack phase aims to destabilize the target or the more established platform.
In the last leg of the attack, the attacker aims to consolidate gains by retaining new users, offering higher incentives, and maintaining the right level of user engagement.
Did you know? The 1inch attack on the blockchain protocol Bancor is one of the lesser-known vampire attacks in crypto. 1inch, earlier tagged Mooniswap, aimed at offering better conversion-specific price efficiency compared to Bancor, siphoning off some of Bancor’s liquidity.
It is worth noting that vampire attacks aren’t all bad for users. Instead, vampire attacks in crypto bring in new players with better yields and incentives, which spoil the regular user for choices. Simply put, a worthy vampire attack creates a win-win situation for users.
Famous vampire attacks in crypto
Still unsure as to what a vampire attack means in crypto terms? Here are a few examples to nudge you in the right direction.
Example 1: LooksRare attacking OpenSea
In 2022, LooksRare — an NFT marketplace — showed up, openly targeting the user base of the then-established Opensea. The incentives, in this case, included 120 million native tokens — LOOKS — being airdropped. However, LooksRare asked people to list an NFT on its marketplace to claim the airdrops.
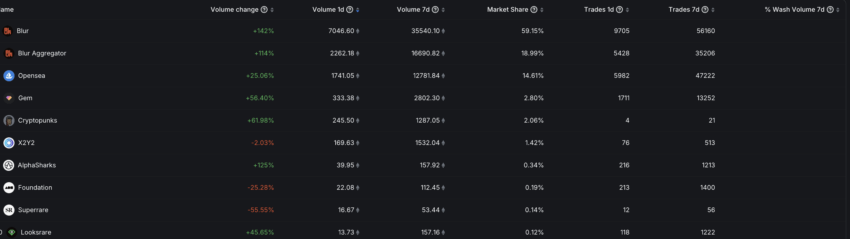
As a result, LooksRare’s trading volume and network activity surged, almost tripling that of OpenSea at that time. At present, OpenSea is trying to fend off a relatively successful vampire attack from Blur.io, another NFT marketplace.
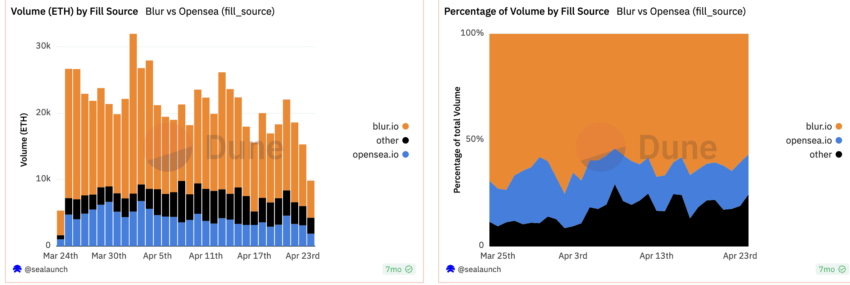
Example 2: SushiSwap’s attack on Uniswap
SushiSwap, a fork of the older DeFi protocol, Uniswap, launched an attack on the latter by launching its native SUSHI token. It promised higher ROI, extending 1000 native SUSHI tokens per Ethereum block. SushiSwap attacked specific Uniswap pools like YFI-ETH and LINK-ETH, the ones where users preferred higher APYs.
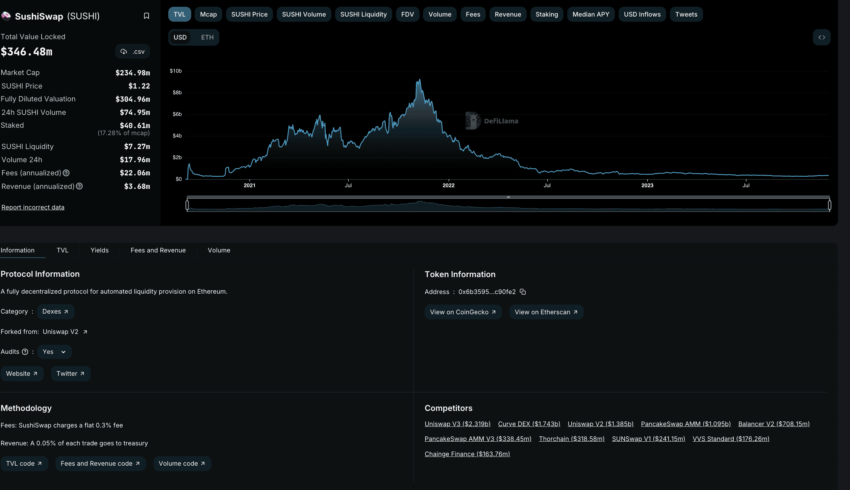
The result of this attack was evident. SushiSwap immediately saw a rise in liquidity despite Uniswap coming back to the top as the market leader. SushiSwap saw pools of money flowing into its liquidity pools. However, as the incentives are attractive, Sushiswap’s presence created a win-win situation for the users.
“Uniswap is the most exciting company in DeFi:
1. It’s actually decentralized
2. It came out of the SushiSwap “vampire attack” stronger.”
Aakash Gupta, VP of Product at Apollo.io: LinkedIn
Example 3: Pools.fyi and Balancer
For the unversed, Balancer is the more popular offering here, offering automated portfolio management services and liquidity provisioning. Pools.fyi — a liquidity pool aggregator — launched an attack on Balancer by helping users locate more profitable pools. Even though the attempt didn’t actually challenge Balancer’s position in the market, it still counted as an attack.
Other examples include 1inch attacking Uniswap, Pancakeswap attacking Uniswap, and even Swerve attacking Curve Finance — its parent chain. These examples show that while DeFi is the more popular space for encountering vampire attacks in crypto, even the NFT space and other use cases aren’t immune from such acts.
How do AMMs and DEXs further attacks?
The inherent nature of automated market makers and decentralized exchanges plays a major role in making vampire attacks in crypto highly profitable.
Let us start with AMMs. These market makers ditch the legacy order book models and bring in liquidity pools. These pools, however, need to incentivize the liquidity providers, who add funds to the pools for seamless operations.
If the pools grab less attention, there will be fewer funds in them; hence, there will be less interest from passive income generators and traders. Also, with low liquidity in sight, fewer trading fees are generated, negatively impacting the liquidity providers.
Even decentralized exchanges are liquidity-driven in that regard. If a DEX has high liquidity, you, as the trader, will have to account for lower slippage and spread. The importance of liquidity, therefore, makes vampire attacks more relevant.
New projects, AMMs, or DEXs, promising higher APYs and lower spreads to users, can pull liquidity out of the established names. And as the DeFi space is still relatively nascent, some marketing and publicity can paint the attackers in a better light. To sum up, while one purpose of a vampire attack is to make the new protocol or platform more popular, the primary aim is to weaken or destabilize the more established players.
Overall, pulling a vampire attack in the DeFi space makes more sense as the space is rife with passive income seekers, and liquidity plays a major role.
How do you stop a vampire attack?
Vampire attacks can drain pools and ecosystems. But there are ways of preventing vampire attacks from wreaking havoc. Here are some of the highlighted threat mitigation strategies.
Having lock-in periods
This concept works wonders for maintaining the health of liquidity pools. This way, liquidity providers cannot withdraw funds from the pools and invest them elsewhere. More established DeFi protocols that offer higher APYs can use this strategy to thwart vampire attacks. An added incentive could be the compounding of the LP tokens or rewards, further discouraging the mercenary behavior.
Restrictions on token withdrawals
In case you do not want to have lock-in restrictions, you can implement restricted token withdrawals. Limited token withdrawals can be either quantity-bound or time-bound. This approach prevents the mass exodus of liquidity.
The concept of dynamic rewards
While restrictions can work nicely, nothing beats the concept of incentivizing liquidity. For instance, a protocol can introduce the concept of dynamic rewards where the users are incentivized based on the duration of liquidity, the amount, and other parameters. This way, established protocols can create a loyal user base, ensuring that users have something profitable to remain engaged for longer periods.
Voting mechanisms and governance
Involving the protocol users with governance gives them another reason to stay. Here, the users are incentivized to make community-specific decisions, possibly making it less tempting to jump ship.
Token vesting
Protocols offering rewards to users can follow the vesting plan. This way, the rewards get credited over time, incentivizing users to stick to the existing protocol long-term. Token vesting is a tried and tested approach to make users remain committed to the ecosystem.
It is worth noting that token lock-ins, vesting periods, and other restrictions can be implemented within the protocol-specific smart contract(s).
Can protocols and projects be made vampire-proof?
Unlike phishing or standard hacking attempts, vampire attacks in crypto cannot be stopped. However, with the strategies listed in this guide, attempts to kill more established platforms can be thwarted.
Besides the implementations, concerned protocols can invest time and effort in building a robust and secure crypto infrastructure — a reason significant enough for most users to remain loyal instead of veering off toward the attacker.
Frequently asked questions
What is vampire mining?
Is SushiSwap a fork of Uniswap?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




