Whether you are a trader, long-term investor, or developer, crypto wallet security is of the utmost importance. It can be tempting to jump head-first into trading before learning how to secure your crypto. Despite the risks, it is easy to assume that hacks could never happen to you. However, they can and they almost certainly will unless you follow these essential crypto security wallet tips.
KEY TAKEAWAYS
➤ In crypto, no one is immune from hacks— not even businesses and legacy protocol developers.
➤ It is essential for everyone to prioritize crypto wallet security to protect their assets.
➤ Use reputable wallets, strong and unique passwords, and enable 2FA to protect your funds.
➤ Regularly update wallet software, use secure internet only, and store private keys offline to prevent breaches.
9 essential crypto wallet security tips
1. Choose a reputable wallet
Types of wallets
You are probably already familiar with the different types of wallets, but let’s recap. Crypto wallets can be categorized in multiple ways: hot and cold wallets, software and hardware wallets, and custodial and non-custodial wallets.
- Hot wallets — maintain a constant connection with the internet
- Cold wallets — do not maintain a connection with the internet and store your private keys offline
- Software wallets — are applications that run on a phone, tablet, or computer
- Hardware wallets — are devices specifically built to hodl crypto
- Custodial wallets — are maintained by centralized companies
- Non-custodial wallets — the user has sole custody of their private keys
Some hot wallets are also software wallets and custodial or non-custodial wallets. Likewise, cold wallets are typically non-custodial and hardware wallets.
These features help users evaluate their specific security needs. As a rule of thumb, cold, hardware, and non-custodial wallets are the safest.
Wallet reputation and reviews
Naturally, if a wallet receives consistently bad reviews, it is a tell-tale sign to stay away. However, you must evaluate the weight of the reviews. If most of them revolve around a wallet’s user interface, it’s probably not the biggest security risk. On the other hand, if the reviews cite a bad random number generator (RNG), this is a huge red flag.
2. Use strong and unique passwords
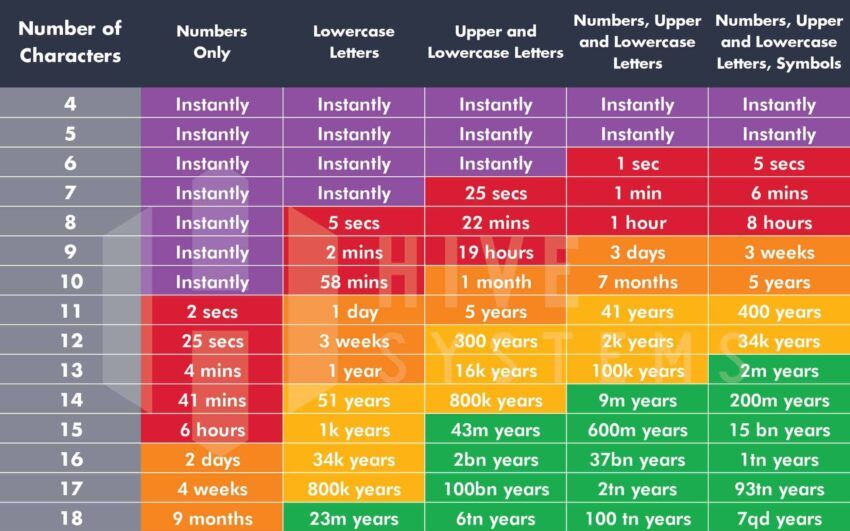
Password best practices
You should use a good password in all areas of activity but especially regarding crypto wallet security. The image above shows how long it takes to brute force a password. The longer the password and the more variation in letter case, symbol, and numbers, the longer it takes to crack your password.
As a rule of thumb, it is best to rotate passwords regularly. Malicious actors on the dark web often sell personal information, including passwords. Additionally, centralized companies incur data breaches regularly, so your passwords could be floating around on the internet, waiting for someone to use them.
Centralized companies should SALT your passwords before placing them in storage. Password salting is a way to protect passwords in storage by hashing them with random bits of data. A company should never store your password in plaintext.
Password managers
A password manager is a great way to keep track of your passwords. With one, you do not have to remember every password, allowing you to use strong and unique passwords without reusing them.
Some password managers come with password generators, which are excellent for creating strong passwords.
While Google accounts offer password managers, using a dedicated password manager is better. That’s because Google is a centralized company, making it a single point of failure. Moreover, the organization often suffers data breaches.
3. Use two-factor authentication (2FA)
2FA methods
Two-factor authentication (2FA) or multi-factor authentication (MFA) provides an extra layer of security to your crypto wallet. MFA or 2FA is an authentication method that requires multiple steps for a user to prove knowledge or possession to gain account access. You likely use 2FA daily when logging into an account with a PIN and password.
Most crypto wallets that use 2FA are custodial. The Exodus and Crypto.com wallets are examples of wallets that use 2FA in some form.
Authenticator apps
An authenticator app is a supplementary app that allows you to prove your identity to an application or service. They generate unique one-time passwords (OTP) or PINs.
Many authenticator apps are time-sensitive, meaning you have limited time to use the OTP before it expires. The app will typically send a code directly to your phone so that you can log in.
At the moment, there are not many MFA crypto wallets, as they require centralized services. According to imToken’s 2023 Crypto Wallet Report, more users would be willing to use custodial wallets if they enabled MFA.
4. Keep your wallet software updated
Regular updates
Always keep your wallet software updated. You should do this as a best practice but also be aware of fake updates. This has happened to both Bitcoin wallet Electrum and Solana’s Phantom wallet. Fortunately, fake wallet updates are not typically how funds are stolen from wallets.
Security patches
Crypto wallets may undergo regular updates to fix security patches. As stated before, code audits help discover critical vulnerabilities in wallets, but this is sometimes not enough. Bugs can pop up later on. Most projects will not divulge the bugs immediately but will offer a patch without exposing the nature of the vulnerability.
5. Use secure internet connections
Avoid public Wi-Fi
Most operational security (OPSEC) experts will tell you never to use public Wi-Fi. Public Wi-Fi networks may expose users to potential security risks as hackers can insert themselves between you and the connection point, allowing your device to communicate with a potential exploiter.
Similarly, it isn’t the best security practice to transact with your crypto wallet publicly — at least for now. When crypto adoption becomes more mainstream, this may change. Regardless, making crypto transactions while connected to public Wi-Fi is not advisable.
VPN usage
A virtual private network (VPN) can assist you in circumventing geographical restrictions for online services. It can also anonymize your online activity and prevent hackers and marketers from tracking you or gaining access to your personal information.
6. Store private keys offline

Cold storage methods
Cold wallets are synonymous with cold storage. When you use cold storage, your private keys are stored offline. Hot wallets like MetaMask store your encrypted private keys in the browser. Contrary to popular belief, your wallet does not actually hold your crypto; it only generates and holds your private keys.
Using cold storage is much safer than using hot wallets. Hot wallets are vulnerable to online attacks because they are connected to the internet. They are more convenient for using decentralized applications (DApps), while cold wallets are less convenient for such use cases.
Hardware wallets
When it comes to crypto wallet security, hardware wallets are top-of-the-line. Hardware wallets are made specifically for cold storage solutions. They typically look like a USB drive, are lightweight, and connect to a PC.
However, hardware wallets also come with a caveat. If the computer you connect your hardware wallet to is compromised, it presents a vulnerability to the hardware wallet.
7. Regularly back up your wallet
Back up options
Another crypto wallet security practice is backing up your wallet. There are multiple ways to back up your crypto wallet. You are likely most familiar with the method popularized by Bitcoin Improvement Proposal 39 (BIP-39), or seed phrases. But there are other unique ways to back up your wallet.
You can always physically write down your private keys (also known as paper storage), although this is not recommended for beginners.
Back up storage options
An increasingly popular backup method is recovery files. You create an encrypted recovery file, store it on cloud services like Google Drive, Dropbox, or iCloud, and use it to restore your wallet. However, storing sensitive data in the cloud carries risks.
Another method gaining traction is multi-party computation (MPC). MPC splits your private key into portions—one stored locally and the other remotely. While convenient, this introduces counterparty risk with storage providers.
There are also unique backup methods like NFTs, QR codes, or even social recovery, where family or friends help restore your wallet. These options are less common and may not always be as secure.
8. Be cautious of phishing scams
Recognizing phishing attempts
Phishing is a form of social engineering. When used, the attackers present themselves as legitimate services, businesses, institutions, or applications.
They sometimes email, message, call, or create fake websites to lure victims into downloading malware or sending sensitive information. The example below is a tweet of a fake Arbitrum airdrop.
Protecting against scams
If you want to avoid these types of scams, you should only download or use services from official websites. Google Play, App Store, or Microsoft Store are examples of platforms that vet applications.
Another way to avoid phishing scams is to avoid giving sensitive information or a significant amount of capital.
You should also stay vigilant of fake technical support messages and DMs out of the blue for trading bots and investment opportunities.
9. Limit your exposure by using multiple wallets
Diversifying risk
Another method of crypto wallet security that is often overlooked is risk diversification. You should have multiple wallets for different uses. For example, if you like to test new technology and are constantly connecting to new decentralized applications, you should have a burner wallet.
With this wallet, there is no real capital at stake. You can have another wallet for liquidity mining and yield farming. It’s all about your personal needs.
With wallets like MetaMask or Brave, you can create as many wallets or browser instances as you need within minutes. They are completely separate from each other and minimize risk.
Importance of crypto wallet security

The year 2022 saw the largest extraction of value from crypto users from security hacks. According to blockchain security firm Chainalysis, hackers stole approximately $3.8 billion in crypto, mostly from DeFi protocols and centralized businesses.
Then, reports emerged in early-2013 that Bitcoin developer Luke Dahsjr lost $3.6 million worth of crypto to a hacker. Similarly, renowned market maker, Wintermute, lost $160 million due to a DeFi exploit.
The most important thing to remember is that no one is immune from hacks, even businesses, and legacy protocol developers.
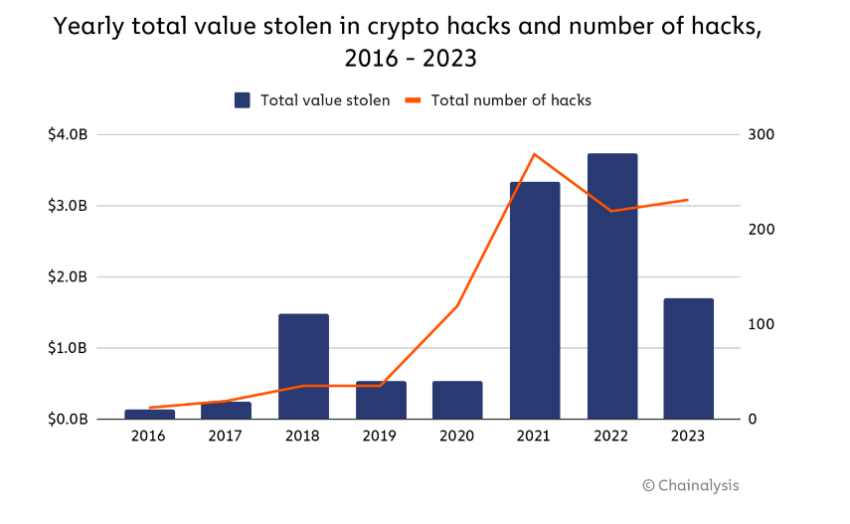
Meanwhile, data from TRM Labs revealed that the severity of online crypto heists has further intensified in 2024. According to the blockchain research firm, hackers stole $1.38 billion in crypto between Jan. 1, 2024 and Jun. 24, 2024. That’s more than double the $657 million stolen during the same period last year.
Safest crypto wallets in 2024
Safepal
Through encrypted QR code communications, the SafePal App establishes a connection with a SafePal S1 hardware wallet. Your cryptocurrency is actually stored on the blockchain and managed via the SafePal App. It does not use WiFi, Bluetooth, or NFC technology.
1. Select the crypto On the Asset page within the SafePal App
2. enter Wallet Detail page
3. Next select Receive enter the Receive page.
Network gas fees
- A self-destruct mechanism designed to protect against malware attacks
- Fairly priced
- NFT storage
- Fairly new
- Not open-source
Nexo Wallet

The Nexo Wallet allows you to manage your balances across multiple wallets with one identity. It allows you to interact with multiple blockchains, such as: Ethereum, Polygon, Avalanche, Fantom, and BNB chain. The wallet also allows you to make cost efficient swaps and save on gas fees with batch transactions.
1. You will need to create one of the following wallets: Metamask, Coinbase, Brave wallet.
2. Sign into your Web3 wallet (Metamask, Brave, or Coinbase wallet).
3. Connect your wallet to Nexo Wallet, or import your wallet, or select Create Wallet to generate a new one.
4. Click on Receive
5. Check that both the blockchain and coin of choice are supported by the wallet.
6. Copy address to receive in Nexo Wallet.
Only nework gas fees
- Supports multiple blockchains
- User friendly
- Aggregates multiple wallets to create Web3 identity
- Not open source
Mobile Wallets
ZenGo
ZenGo is one of a few new wallets that use multi-party computation, a way of securing your wallet. It also allows you to connect to your favorite DApps that support WalleConnect. The wallet also features a recovery kit for securing your assets, instead of seed phrases.
1. Login to your ZenGo Wallet.
2. Select your token of choice.
3. Click the Buy button.
4. Select the third-party payment provider of your choice.
5. Press Continue and follow the instructions.
Banxa spread fees: 1.99%
Banxa Debit/ Credit, Apple/ Google Pay: 3%
Moonpay spread fee: 1.5-3%
Changelly processing fee: 0.5%
Network gas fees
- Third-party payment providers in app
- Supports NFTs
- WaletConnect integration
- Limited functionality
- Limited blockchains support
Exchange Wallets
Bybit Wallet

Bybit Wallet is a product of the global exchange Bybit. It alows you to buy and convert cryptocurrencies. It is also a DApp aggregator.
1. Login to your Bybit account and Bybit wallet.
2. Select Deposit.
3. Select Spot.
4. Choose a cryptocurrency.
5. Follow instructions.
Network gas fees.
Bybit’s fees when using spot and derivatives features.
- Web3 app aggregators
- Allows you to trade spot and derivatives
- Custodial
Binance Chain Wallet

Binancce Chain Wallet is a Web3 wallet that interacts with the BNB chain. It is the equivalent to Metamask for the BNB chain. This means that user can interact with DApps on the BNB chain.
1. Create a Binance Chain Wallet.
2. Select a payment provider or one of your wallets that has cryptocurrency to transfer.
3. Select Receive.
4. Copy the address.
5. Send crypto.
Network gas fees
- Gives you access to DApps on BNB chain
- Allows you to connect to EVM-compatible blockchains
- Uses a threshold mechanism for private key storage, which means it is custodial
Coinbase Wallet

Coinbase Wallet has multiple features. When you create a wallet you have the option to claim a domain name, free of charge. In addition to buying and trading crypto, it also features a browser, has a browser extension, and allows you to connect to DApps.
1. Sign in to your Coinbase Wallet.
2. Choose a payment provider or a wallet to transfer crypto from.
3. Go into Coinbase Wallet and select Receive.
4. Select a chain and copy your address.
5. Send crypto.
Network gas fees
- Allows you to connect to DApps
- Supports multiple blockchains
- Features a browser
- Open-source
- May be difficult for beginners
Kucoin Wallet
Kucoin Wallet is a cryptocurrency that allows you to send and receive crypto. However, it also gives you access to the Kucoin exchange. The wallet also supports multiple cryptocurrencies.
1. Login to Kucoin Wallet.
2. Select Deposit.
3. Copy the address.
4. Send cryptocurrency.
Network and gas fees, otherwise, fees associated with using Kucoin exchange’s services.
- Supports NFTs
- Gives you access to DeFi
- Supports multiple cryptocurrencies
- Not open-source
Hardware Wallets
Ledger

Ledger has an industry reputation for being trusted and reliable. Since its inception, it has not been hacked. The wallet uses Bluetooth technology as opposed to NFC technology.
1. Open the app and navigate to your account.
2. Select Transfer.
3. Select Withdraw.
4. Select External Wallet.
5. Select Add Wallet Address.
6. Select the Network and paste your Ledger account address.
Network gas fees
- Supports multiple cryptocurrencies
- Smart phone app
- Bluetooth
- Not fully open-source
Trezor

Trezor wallets are designed to have PINs that remain even if their host computers are compromised. Their PINs also have in-built systems that prevent brute force attempts. Also, after every incorrect attempt, the waiting time to log into a wallet is raised by a power of two.
1. Select Pay with and choose the cryptocurrency that you want to send to your Trezor.
2. Paste the address you copied from Trezor Suite in the ‘To’ field.
3. Write an optional note.
4. Click Continue.
Network and gas fees
- Secure
- Easy to use
- Supports multiple cryptocurrencies
- Not available on IOS
Keep your funds safe
If you practice these nine crypto wallet security tips, your funds are much safer than if you did not. Remember, every user is their own biggest risk. The more you educate yourself on crypto, the smaller that risk becomes. Staying informed about the latest threats and best practices can be a huge advantage when it comes to securing your crypto.
Frequently asked questions
How safe are crypto wallets?
Which crypto wallet has the best security?
How can I protect my crypto wallet?
Are crypto wallets monitored?
Can someone steal your crypto wallet?
Can a crypto wallet crash?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.






