The life of a regular crypto trader isn’t easy. SEC crackdowns, rug pulls, and FUD-driven sell-offs are enough to scare off any individual holding digital assets on a centralized exchange. And yes, the FTX contagion is still fresh on our minds. With threats and concerns aplenty, in 2023, it makes the most sense to store your crypto in self-custodial cold wallets. As a risk-averse individual, you can go one step further and opt for air-gapped wallets — cold wallets with advanced security traits.
This guide delves deep into the world of air-gapped crypto wallets, covering how they work and the associated benefits and challenges.
- Private keys: the driving force behind crypto wallets
- What are air-gapped wallets?
- Is an air-gapped wallet safe?
- How do air-gapped wallets work?
- Why use an air-gapped wallet?
- Setting up an air-gapped crypto wallet
- Air-gapped crypto wallets and types
- Understanding the threats associated with air-gapped wallets
- What is a keyless wallet?
- Air-gapped vs. keyless wallets: compared
- Comparing air-gapped wallets and hot wallets
- Challenges and criticisms of air-gapped wallets
- What could the future be for air-gapped wallets?
- Are air-gapped crypto wallets foolproof?
- Frequently asked questions
Private keys: the driving force behind crypto wallets

A crypto wallet doesn’t actually store your crypto assets. Instead, it stores your private keys while the actual crypto assets reside on the blockchain. With these private keys, you can sign transactions. These might involve withdrawing crypto, moving assets from one wallet to another, or paying for using any chain-specific service.
What are air-gapped wallets?
Air-gapped wallets are cold storage wallets at heart. You can think of them as air-gapped hardware wallets.
However, the wallets are completely disconnected from the internet or the wireless world, making them akin to physical, minimally interactive devices that store your private keys. Some partial air-gapped wallets do not connect to Bluetooth, Wi-Fi, NFC (Near Field Communication), or any other wireless medium. And then some fully air-gapped models do not even support USB connections.
Take Ledger’s Nano X, for example. Despite being an excellent hardware wallet, Bluetooth support might make it a tad vulnerable to threats. Even though Ledger emphasizes top-notch security, concerns related to Bluetooth interception and pairing vulnerabilities might still linger. That is where air-gapped wallets come to the rescue, as they work in isolation.
Fully air-gapped wallets have zero wireless liaisons. The offline and isolated environment makes them immune to malware, phishing threats, and hackers. Note that the term air-gap refers to how these wallets are distanced or gapped from any wireless network — more like insulation against exploits.
Do note that “air-gap” is a computer security term referring to the complete isolation of a device or a network from other networks or devices. The gap, or rather an isolation, is “full of air.” Even an air-gapped computer is possible if it doesn’t have any ports and if it doesn’t support any form of wireless communication. An air-gapped hardware wallet follows the same concept.
Get the secure, air-gapped hardware wallet — NGRAVE. Shop now!
Is an air-gapped wallet safe?
An air-gapped wallet provides a higher level of security when compared to a hot wallet like MetaMask or Trust Wallet. The safety-specific offerings also stand out against other cold wallets. Especially those that can connect to the internet or any wireless network.
While the disconnected state of the wallet is a prime factor, the reason lies somewhere underneath. These wallets never connect to wireless networks, so signing transactions with them is far more complex.
The below tweet shows why wireless networks can get you into muddy waters.
How do air-gapped wallets work?
With any crypto wallet, if you need to process a transaction, you must sign and broadcast the signed transaction — something an air-gapped wallet does differently.
Preparing a transaction
When you create a transaction on any internet-connected device, say your computer or smartphone, a device-specific component of your air-gapped wallet creates a “watch only” entity. This way, you can generate a new address and feed in all the transaction details but cannot sign the transaction. With a hot wallet or a Wi-Fi, NFC/Near Field Communication, or Bluetooth-connected cold wallet, you could have forwarded the intimation and signed it. This isn’t possible with air-gapped wallets.
Instead, you need to transfer the details of the transaction to the air-gapped wallet as a file that the wallet can read.
Confused about how to transfer a transaction to a wallet? Here’s an example:
Imagine using the Coldcard wallet — one of the more popular air-gapped options. The first step, as mentioned above, is to create a transaction. For that, say you use a bitcoin wallet, Electrum. This wallet is connected to the internet. At this point, you can feed in the recipient’s address and the value of the BTC you want to send. This is when a transaction is created.
Signing the transaction
On Electrum’s interface, you will then have the option to save the transaction created inside the bitcoin wallet. Upon saving, The format you get is a Partially Signed Bitcoin Transaction (PBST). You can shift these partially signed bitcoin transactions to a MicroSD card. Then, you can connect this card to the air-gapped wallet.
Did you know? A Partially Signed Bitcoin Transaction or PBST is a wallet-specific format that was originally introduced by Bitcoin Improvement Proposal (BIP) 174. While a PBST is created in a binary format, it is represented in the Base64 format or the binary-to-text format for wallet-to-wallet transmission.
This approach of moving a half-cooked transaction from a computer-specific wallet to something isolated like a Coldcard is termed “Exporting the transaction.”
You can now open this exported transaction on your air-gapped wallet. If you are specifically using Coldcard as the wallet, you will see a “Ready to Sign” option. This will open the PBSTs or Partially Signed Bitcoin Transactions, which you can sign using your private key. On signing, the wallet saves the ready transaction on the MicroSD itself as a new PBST file that the online device can read.
Broadcasting the transaction
After this, you will need to eject the MicroSD card, connect it to the online computer, take the new PBST transaction, and load it to the online wallet. This way, you can broadcast the signed transaction.
It is essential to note that storing and exporting transactions using a MicroSD card is only one way of interacting with an air-gapped crypto wallet. Also, the exact process and steps depend on the type of online and air-gapped wallet you are using.
Use the secure air-gapped signing feature of the Ballet wallet today. Try it now!
Using QR-code base transmission for your air-gapped wallet
As mentioned earlier, exporting a new transaction to an air-gapped wallet using a MicroSD card isn’t the only way to interact. You can even use the QR code scanner on your air-gapped wallet to scan the transaction from the computer and sign it using the key.

This will generate new QR codes representing signed data. You should now use your online device to scan and decipher the QR codes by extracting the signed transaction and eventually broadcasting the same.
Did you know? Data moved using QR code scanning involves an optical mechanism where you capture the image and use the device itself to extract the data. There isn’t any kind of network connectivity involved unless the QR code opens an online link.
Why use an air-gapped wallet?
Given the market unpredictability and irreversible nature of crypto-related transactions, air-gapped wallets have a vital role to play in the web3 ecosystem and in promoting crypto wallet security
As an air-gapped device is still a lot like a cold storage option, it offers a lot of protection against threats. Here are some reasons to invest in one:
- Safety against online threats
- A better storage location for your private keys
- Peace of mind if you plan on storing your crypto for long.
With an air-gapped wallet, your keys are only yours. You are always in control, and the crypto holdings are always in your custody.
The below thread enlists some benefits of an air-gapped hardware wallet.
And in the wake of the FTX contagion, web3 users were once again reminded of the most important motto in crypto.
In light of another exchange meltdown, “Not your keys, Not your coins” is again relevant.
Andreas M. Antonopoulos, best-selling author of Master Bitcoin and The Internet of Money: Twitter
Setting up an air-gapped crypto wallet
The wallet software, containing specialized cryptographic algorithms, manages everything. Here’s how to set up an air-gapped wallet:
- The first step involves selling up a 12-word or a 24-word seed phrase. Also termed the recovery phrase, the software of your air-gapped wallet creates and generates this secret set of words. The seed phrase works as the root that eventually helps generate the private key. You can even use this seed phrase to recover your key(s) if you lose device access.
- The seed phrase now becomes the key-generating input for your wallet. The algorithm that takes the seed phrase as feed is typically HMAC-SHA512. This algorithm then generates a large, random number, which becomes your private key.
- After the private key is generated, also referred to as the air-gapped key, the wallet’s software uses the “Elliptic Curve Multiplication” mechanism to derive the public key. Do note that the Elliptic Curve Multiplication is strictly a one-way mechanism. It cannot be used to generate private keys from public keys.
- At this point, your public key is encoded and hashed, becoming your wallet address in the process. You can share this wallet address with anyone.
- In the meantime, your private key remains safely tucked inside the air-gapped wallet, usable only for signing transactions on the device.
A good approach is to write down the seed phrase or the mnemonic phrase somewhere secure beforehand. This might help you with wallet recovery if needed. Note that you should never store any kind of seed phrase online, not even with encryption.
Air-gapped crypto wallets and types
Air-gapped crypto wallets are basic devices with no fancy connectivity traits. Therefore, you can categorize them as follows:
Hardware wallet
To be specific, every air-gapped wallet is a hardware wallet, but not every hardware wallet is air-gapped. The idea here is to pick something like a Coldcard wallet or an Ellipal Titan that is fully air-gapped and doesn’t have fancy traits like Bluetooth support.
If you seek the strongest form of encryption in an air-gapped wallet, NGRAVE ZERO is another name to consider. It is fully air-gapped, offers EAL7 certification, and supports biometric authentication.
Paper wallet
If you are on a budget, nothing beats using a paper wallet as your air-gapped wallet. This is where you take a printout of your private and public keys as encoded QR emblems. You simply scan the QR code on the paper with your online device to sign the transaction. A good strategy here is to use one paper wallet only once, as sweeping funds from the keys stored on it can comprise the same if your online device is under attack.
Bitcoin wallet
A few crypto wallets are air-gapped and only restricted to BTC transactions. While the concept of air-gapping remains consistent, the spread being restricted to BTC adds to the credibility. The Passport from Foundation Devices is an example of an air-gapped bitcoin wallet that works hand in hand with Envoy — the companion online app. The model also features open-source firmware, making the device a solid Ledger alternative. (Ledger, a leading hardware wallet manufacturer, recently drew criticism from the crypto community for its controversial cloud backup update).
Another example of a typical air-gapped bitcoin wallet is Blockstream’s Jade, best known for its price tag and seamless QR code-specific communication.

Multi-sig wallet
Another type of air-gapped wallet is a multi-sig wallet, a device that is still isolated but can generate seed phrases to help to manage other devices. 1inch’s new air-gapped wallet is one such device. It looks like a bank card and comes with a Gorilla Glass 6 layering, an E-ink display, a micro camera, and other nifty traits. You can use one wallet to create and manage others.
Understanding the threats associated with air-gapped wallets
Is this the perfect crypto security solution? Which threats are also associated with air-gapped wallets? Let’s take a look at how an air-gapped wallet works in relation to different models and scenarios.
Scenario 1: Online threats
Having an air-gapped wallet is an adequate solution to this threat scenario. An air-gapped wallet is isolated from networks, which keeps your private keys secure and disconnected from the world.
However, downloading and installing firmware updates is still important to ensure that the wallet keeps working at its highest potential. You can download these on your computer, move the updates to a micro-SD card, and install them directly on the device.
Scenario 2: Physical threats
Imagine someone stealing your air-gapped wallet. That qualifies as a credible physical threat. This is where you might want a device that lets you set an additional line of security as a PIN or passphrase. Selecting a device with multi-sig verification can also be a way out.
Scenario 3: Supply chain threats
Imagine someone tampering with your wallet before it even reaches you. The best way to solve this is to purchase a wallet with a secure element chip. They offer additional protection and are virtually tamper-proof.
Scenario 4: Accidental issues
What happens if you forget the seed phrase and cannot recover the stored crypto? You can prepare for this threat by choosing a multi-sig wallet that allows you to recover crypto if you have access to other verifiers.
Scenario 5: Issues with the online app or the MicroSD card
What if someone hacks into the online app — the one you use to trigger the transaction and generate the same in the first place? Or what happens if the MicroSD card you would use is already injected with malware to infect the air-gapped wallet? Even supplying malicious codes to the wallet using the SD card or infected QR codes is possible. Another kind of risk is QR-code substitution, but for that, a hacker would require access to your computer.
In that case, there are two probable solutions to consider:
You can either get a wallet with a secure element chip that keeps all the threats at bay or a device with a secure display — ensuring you can see and verify every transaction detail, such as the address and the amount of crypto that you are sending. Also, it is advisable to frequently run a malware check on your device to check for threats.
What is a keyless wallet?
Like any other hardware wallet, an air-gapped wallet relies completely on its private key. Or, if you are using a multi-sig wallet, there are a handful of keys to work with. Using advanced cryptography, keyless wallets have started showing up to combat this. They even use the secure multi-party computation (SMPC) technique to make crypto access more complex yet seamless for the person who is actually in charge of the wallet.
The concept is simple: the private key itself is broken into and stored across multiple locations — a smartphone, secure servers, or backup devices. While signing a transaction, every part must come together to validate and work as the complete private key. This approach reduces the risk of accidental losses.
Air-gapped vs. keyless wallets: compared
If you are considering choosing a keyless wallet instead of an air-gapped wallet, the below comparison table is worth a look.
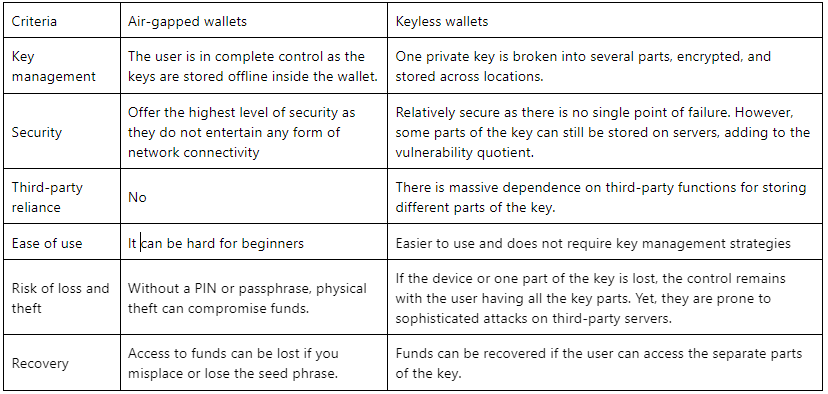
You should carefully evaluate your preferences and choose the wallet that is right for you.
Comparing air-gapped wallets and hot wallets
Still unsure as to how air-gapped wallets differ from your regular hot wallets? Here is another table to nudge you in the right direction:
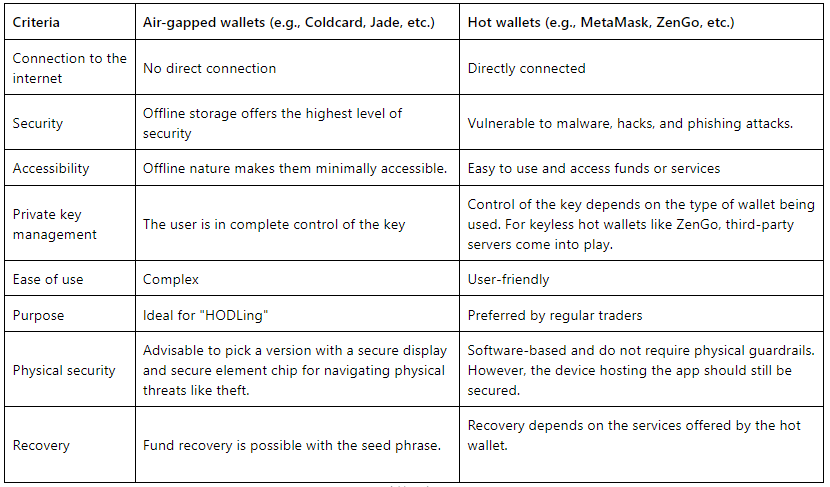
Challenges and criticisms of air-gapped wallets
Air-gapped wallets are useful but do come with a fair share of issues. Here are some of the more pressing challenges:
- Complex learning curve leading to usability concerns
- Still prone to threats related to theft, accidental losses, and more
- The recovery process is fully dependent on seed phrases
- Prone to human error, like incorrect transaction signing
- Time-consuming as signing and broadcasting transactions follow separate curves
- In the absence of a secure chip, they are prone to supply chain attacks
- Supplying malicious code to the wallet using a MicroSD card or an infected QR code is possible
What could the future be for air-gapped wallets?
The challenges concerning air-gapped wallets can be addressed in time, with manufacturers focussing on usability improvements with clearer instructions and highly intuitive interfaces. Water and fire resistance components could be an area of focus to immunize them against physical threats. Multi-sign wallets like the ones from 1inch are already doing their bit toward making key recovery easier.
Other implementations like air-gapping smartphone wallets, implementing measures to combat supply chain threats, and more may also show up in time.
Are air-gapped crypto wallets foolproof?
Air-gapped wallets have changed our view of self-custody. As they are completely disconnected from the internet or any form of wireless communication, online threats do not pose any threats. However, they still need a lot of work when it comes to foolproofing the entire process of signing and broadcasting the transaction.
Yet, with new entities entering the space, including The Passport from Foundation and 1inch’s hardware wallet, the focus remains on amplifying the security aspect of air-gapped wallets and improving user experience.
Frequently asked questions
What is an air-gapped wallet?
What is an air-gapped key?
What is the disadvantage of keyless?
Is keyless better than key?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




