In the crypto market, the strength and resilience of cybersecurity measures remain under constant scrutiny.
Cyber-attacks are scaling up in frequency and sophistication, so cybersecurity experts spotlight the aged crypto infrastructure. This is seemingly becoming the Achilles heel in safeguarding cryptos and information.
Crypto Hacks: It’s All About Cybersecurity
Amer Vohora, the CEO of SwissFortress, shed light on the phrase “antiquated infrastructure” in a recent discourse with BeInCrypto. Vohora elaborated on the monumental challenge the existing cryptocurrency frameworks face. Essentially, it is a persisting reliance on outdated systems.
Despite the quantum leap in technological advancements, the core of cyber defenses, in his view, remains stuck in yesteryears, quite literally dating back to the Satoshi whitepaper from 2008.
The blatant reality is seen in custodial systems for cryptos, where breaches, often stemming from password and phone hacks, have become commonplace.
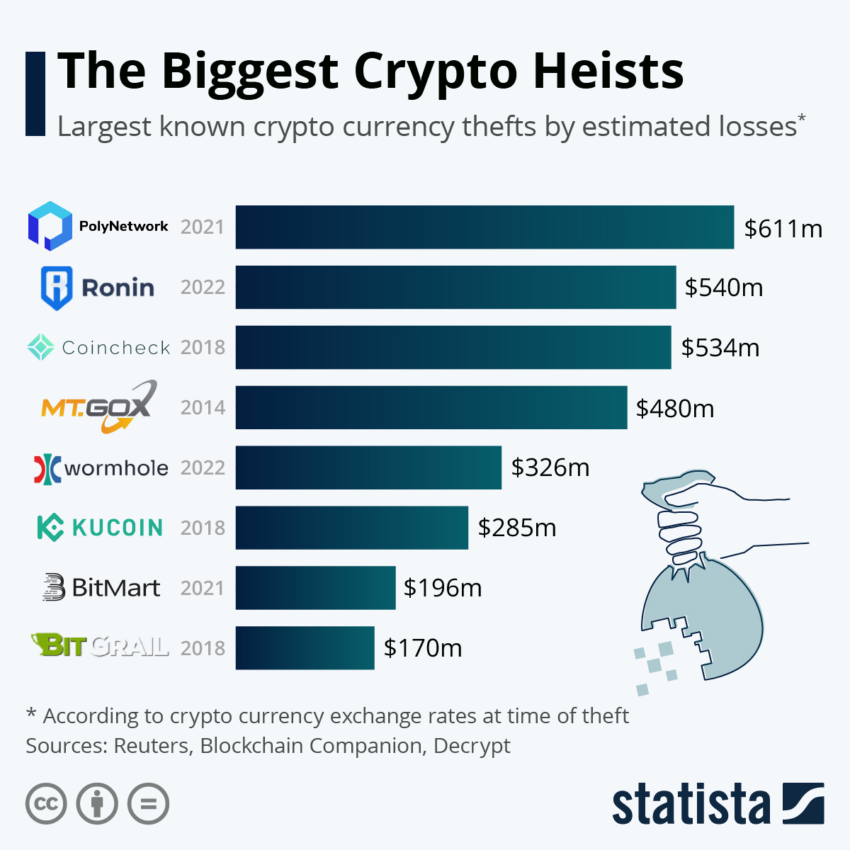
“We are still using the receiving address from the Satoshi whitepaper from 2008, and everyone is forced to use that. This is a hindrance to mass adoption due to the complexity… That same infrastructure has allowed backend theft, misappropriations, Mt.Gox, or FTX-type incidents,” Vohora said.
Vohora articulated a glaring flaw in software security, which is self-trust. When a software component interacts with another, it is assumed that the data or instructions received are trustworthy. There is a need for a radical departure from this model by introducing cryptographic proofs for every operation within the ecosystem.
Read more: 9 Crypto Wallet Security Tips To Safeguard Your Assets
By this mechanism, rather than the software blindly trusting incoming data, every transaction mandates a valid cryptographic proof, mirroring the security principles seen in blockchain transactions.
“[We must] replace username and password-style security with cryptographic proofs for every operation. So when a user does anything, they make a digitally signed transaction similar to an on-chain BTC spend. Still, it can perform any function, such as transferring money between accounts, making payments, signing legal instruments, and purchasing NFTs. So, instead of the software blindly trusting whatever it is told, it always confirms valid cryptographic proof before any given transaction,” Vohora added.
Two harrowing instances cited by Vohora underscore the urgency for an overhaul. Unstoppable Domains and similar platforms, with a public API for address lookup, expose users to potential scraping, revealing their transaction history. Additionally, conventional Two-Factor Authentication (2FA) measures crumble when a phone or SIM gets stolen, exposing the accounts to unauthorized access.
The solution proposed by Vohora is intriguing. It interfaces directly with a custody system via cryptographic proof, embedding an additional physical security layer. Therefore, reimagining the security architecture from the ground up.
“The only wallets that know what addresses they are using are the sending and receiving wallets. Third-party observers cannot know which identity did or did not receive funds,” Vohora stated.
Human Error Remains a Pivotal Factor
In a parallel conversation with BeInCrypto, Ronny Dahan, CEO of SIRKL.io, magnified the inherent liabilities even in revolutionary crypto wallets. While they bring forth an aura of heightened security and user control, Dahan emphasized that the liabilities are far from eliminated.
Human error, spearheaded by phishing scams and private key mishandling, still presents a looming threat.
“Users are solely responsible for managing their wallet’s private keys. If lost or compromised, access to funds can be irretrievably lost. This responsibility can be challenging for non-technical users,” Dahan said.
Dahan laid out a sturdy five-step blueprint to shore up personal and professional digital fortresses as the crypto industry goes through the labyrinth of cybersecurity threats:
- Employing strong passwords.
- Utilizing hardware wallets for offline crypto storage.
- Activating Two-Factor Authentication.
- Staying abreast of the latest hacking methodologies.
- Ensuring regular backups of critical wallet and account information.
Read more: Top 10 Must-Have Cryptocurrency Security Tips
“While Web3 wallets offer greater control and security over traditional financial systems, they come with responsibilities and risks. Users must exercise caution, stay informed, and follow best practices to mitigate these inherent liabilities and limitations,” Dahan added.
The narratives from Vohora and Dahan echo a unified message – the pressing need for a seismic shift in cybersecurity infrastructure. The revelations unveil that while crypto is advancing at breakneck speed, the cybersecurity frameworks in place are akin to trying to catch up to a bullet train on a bicycle.
The stark dissonance between the two calls for an urgent, robust, and forward-thinking approach. This entails a collective move from the “antiquated infrastructure” towards a more fortified, resilient, and modernized digital defense ecosystem.
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


