BlackBerry’s cybersecurity division has identified malware families and tools most prevalent in cryptojacking breaches between March and May.
Cryptojackers, believed to be Russian, attacked Linux-based systems with the open-source tool XMRig and the Prometei botnet.
BlackBerry Highlights Growing Arsenal of Malware Tools
According to BlackBerry, hackers initially unleashed Prometei to Linux-based VMWare ESXi servers in all countries except Russia, Ukraine, Belarus, and Kazakhstan. Later attacks excluded only Russian systems.
Around since at least 2020, Prometei piggybacks off different internet domains, making it difficult to trace and stop. Additionally, the botnet runs on Windows machines.
Hackers used Prometei to mine cryptocurrencies like Monero.
BlackBerry’s team also found that SmokeLoader, categorized as a ‘dropper’ in cybersecurity parlance, is a tool criminals favor to load malware. Distributed through spam and various phishing attacks, SmokeLoader survives reboots and hides itself in legitimate computer operations.
After installation, it can download and load more malware and frustrate quarantine attempts.
Cybersecurity firm SonicWall recently reported that cryptojacking incidents rose 399%year-on-year by the end of June. Hackers targeted the Oracle cloud and also breached macOS devices through HonkBox cryptojacking malware embedded in cracked applications.
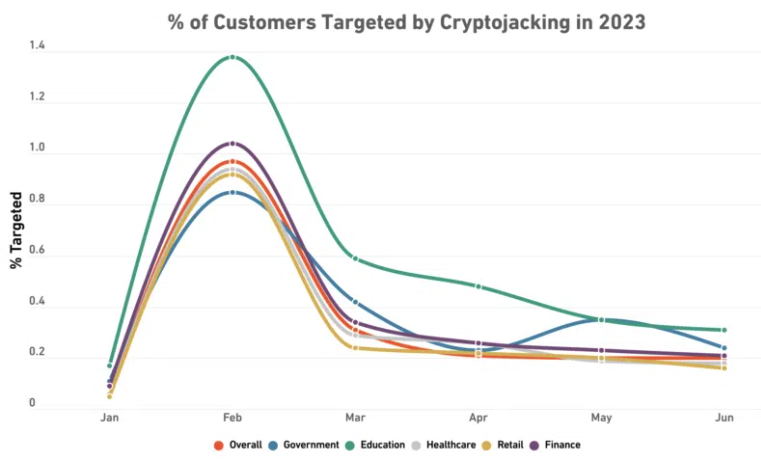
State-sponsored actors in North Korea and other regions facing sanctions or mining bans are often behind cryptojacking.
Malware Tools Target Apple Users
Recently, SlowMist researchers reported a hack intercepting two-factor authentication (2FA) on macOS and iOS devices. The hack allows threat actors to add their number to 2FA authentication methods used to access iCloud.
Once in, hackers can easily access wallet data the user stored on the cloud. Wallet vendor MetaMask warned users earlier this year that default settings on Apple devices stored their wallet seed phrases on iCloud.
Is the new threat landscape too daunting? We round up the best tips for keeping your crypto safe here.
Apple news outlet 9to5mac also recently reported a malicious macOS remote access tool available on the dark web. While not geared specifically towards crypto theft, the tool is believed to “grant full access to Macs,” which could lead to wallets being compromised.
Got something to say about the new malware tools BlackBerry has identified or anything else? Write to us or join the discussion on our Telegram channel. You can also catch us on TikTok, Facebook, or Twitter.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


