Cado Security’s discovery has thoroughly debunked the belief that macOS systems are impervious to malware. This revelation concerns a new malware-as-a-service (MaaS) called “Cthulhu Stealer,” which targets macOS users through deceptive means.
The rise of Cthulhu Stealer indicates that no system is completely secure against cyber threats.
How Malware Steals Mac Users’ Crypto?
Cthulhu Stealer disguises itself as legitimate applications such as CleanMyMac and Adobe GenP and software claiming to be an early release of “Grand Theft Auto VI.”
Once the user mounts the malicious DMG file, they are prompted to enter the system and MetaMask passwords. This initial deception is just the beginning.
Read more: A Guide to the Best AI Security Solutions in 2024
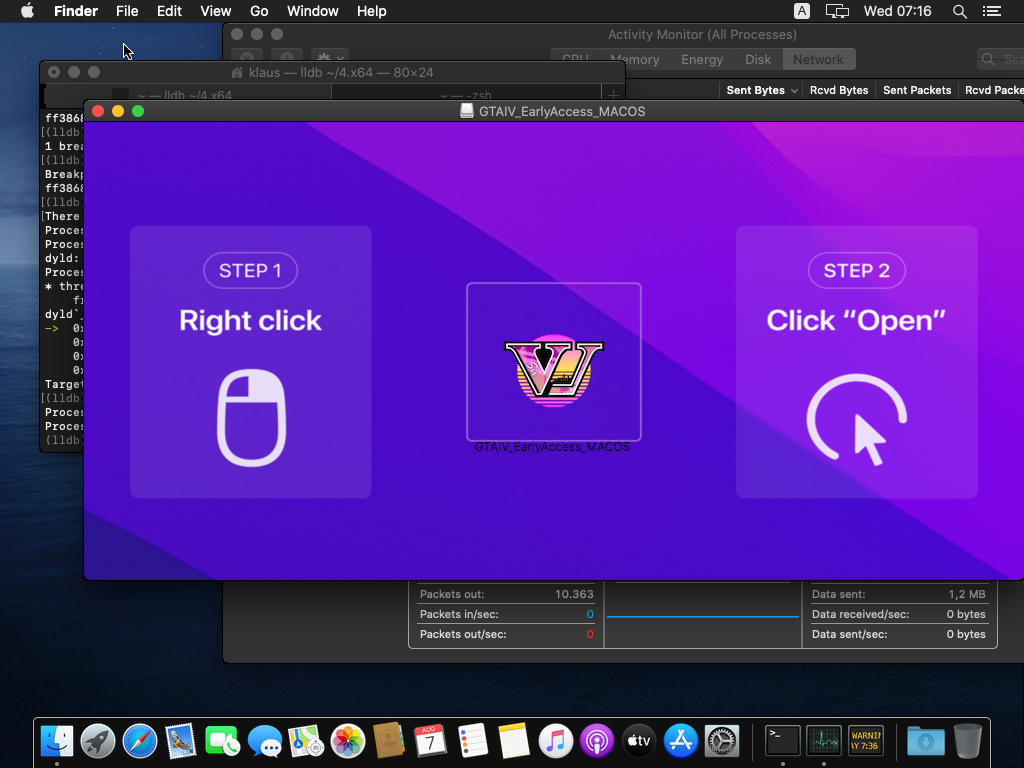
Following the credentials input, the malware utilizes osascript, a macOS tool, to extract passwords from the system’s Keychain. This data, including details from crypto wallets like MetaMask, Coinbase, and Binance, is compiled into a zip archive. This archive, identified by the user’s country code and the time of the attack, contains the stolen information.
Cthulhu Stealer also steals data from other platforms, including:
- Chrome extension wallets
- Minecraft user information
- Wasabi wallet
- Keychain passwords
- SafeStorage passwords
- Battlenet game, cache, and log data
- Firefox cookies
- Daedalus wallet
- Electrum wallet
- Atomic wallet
- Harmony wallet
- Electrum wallet
- Enjin wallet
- Hoo wallet
- Dapper wallet
- Coinomi wallet
- Trust wallet
- Blockchain wallet
- XDeFi wallet
- Browser cookies
- Telegram Tdata account information
Moreover, Cthulhu Stealer collects detailed system information such as IP address, system name, and OS version. It then sends this data to a command and control (C2) server, enabling the attackers to refine their strategies.
Scammers Charge $500/Month For Cthulhu Stealer
Scammers use various strategies to trap the victims into installing the malware. For example, on social media, some scammers pose as employers who offer jobs that require downloading software to track working hours. These offers come with a sense of urgency, pushing the potential victim to download the application quickly.
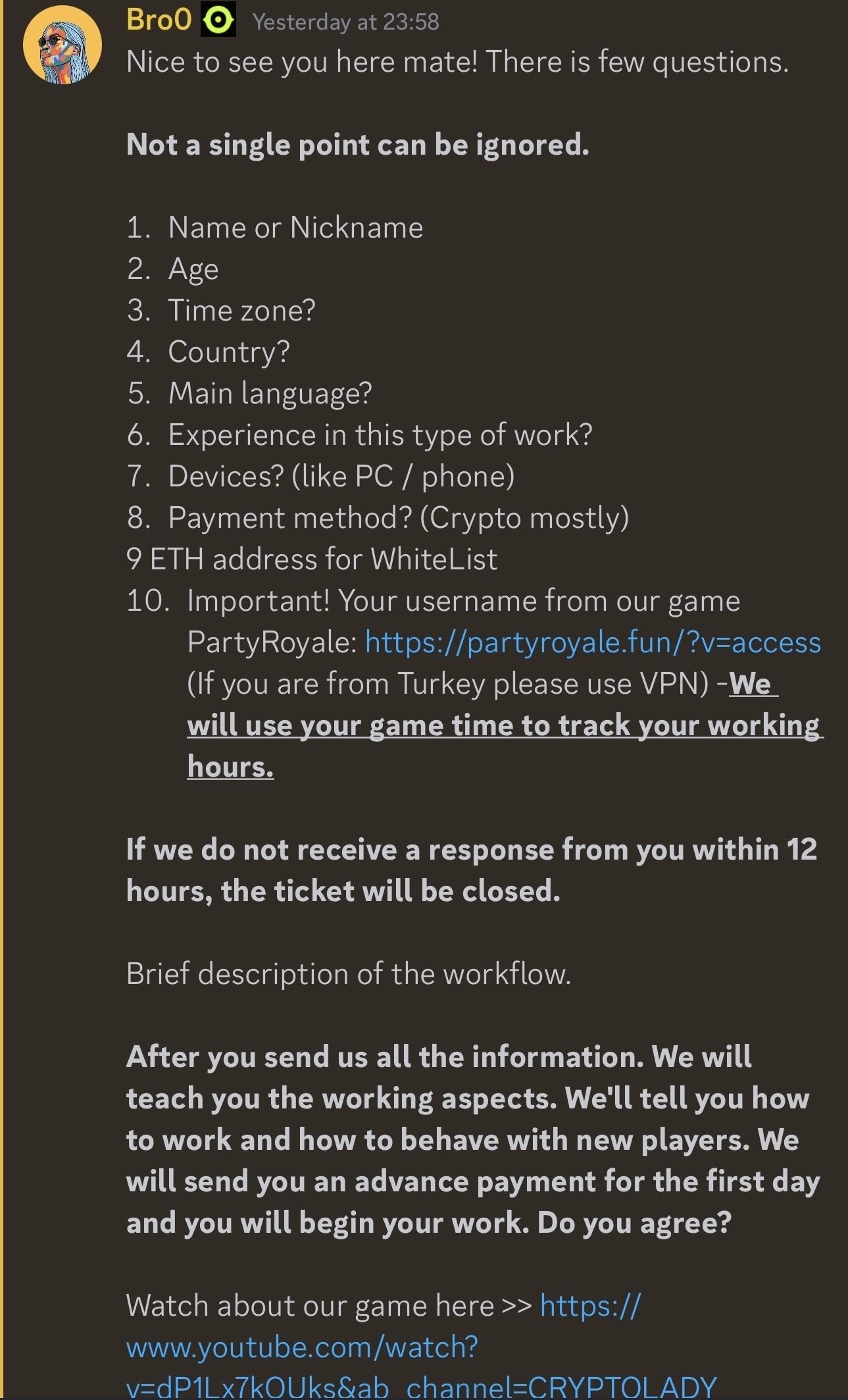
The developers and affiliates behind Cthulhu Stealer, known as the Cthulhu Team, use Telegram to manage their operations.
“The stealer appears to be being rented out to individuals for $500/month, with the main developer paying out a percentage of earnings to affiliates based on their deployment. Each affiliate of the stealer is responsible for the deployment of the malware. Cado has found Cthulhu stealer sold on two well-known malware marketplaces which are used for communication, arbitration and advertising of the stealer, along with Telegram,” Cado informed readers.
Read more: 9 Crypto Wallet Security Tips To Safeguard Your Assets
To protect themselves, users should install reputable antivirus software that is specifically designed for macOS. They should also be cautious of employment opportunities that require immediate software downloads. Regular software updates can further reduce the risk of malware infections.
In a discussion with BeInCrypto, a CertiK spokesperson shared some tips on how individual users and organization adapt their security practices against malware.
“Some of the more effective methods are downloading from the official website or downloading from the macOS App Store; don’t install software from unknown sources. If you did not download from the macOS App Store, after downloading, you need to check whether the hash value of the file is the same as the hash value of the file provided by the official website,” a CertiK spokesperson told BeInCrypto.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.

