Trust on the internet is both a currency and a curse. On the one hand, influencers — the celebrities of the online world — make their millions by building strong relationships with their community. On the other, scammers — the internet’s modern-day highwaymen — take advantage of misplaced trust to exploit their unsuspecting victims.
Trust in technology is another significant factor. Millions of people trust Facebook with their personal and relationship data, Amazon with their home address, and PayPal with their financials. This generally works well until it doesn’t. In the case of cybersecurity breaches of trusted organizations, of which there have been countless examples, the limits of trust quickly become all too apparent. Zero-trust architecture is a crucial blockchain-based solution. Here’s what to know and how it works.
What is zero-trust architecture (ZTA)
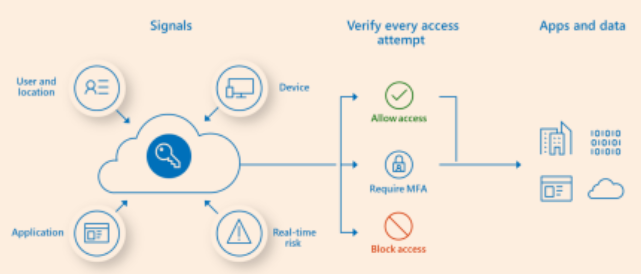
Zero-trust architecture (ZTA) is a concept in web2 cybersecurity that aims to mitigate security risks by eliminating the assumption of trust within networks. The main idea of ZTA, “never trust, always verify,” is about changing old ways of doing things. Instead of automatically trusting everything inside a particular network, ZTA says we should check every request coming in or going out, no matter where it comes from. It’s like having a strict door policy where everyone must show ID every time they enter, ensuring only the right people get access.
Zero-trust architecture changes the game from guarding the borders to watching the individual players. ZTA follows every user, device, or system, verifying their actions no matter where they are. This way, trust is never assumed; it’s always checked, making sure that each interaction is as secure as possible.
The new internet, web3, has its own version of the zero-trust slogan “never trust, always verify.” The Latin phrase “vires in numeris” means “strength in numbers” or, more generally, the power of the number-based cryptography that secures blockchain.
While the traditional understanding of ZTA relates to fundamentally hard-to-secure web2 platforms and protocols, it’s important to understand that this security model is the basis of blockchain technology. That’s the fundamental innovation of blockchain: it inherently embodies zero-trust architecture through cryptographic verification at every step.
Web3: Zero-trust by default
Web3 doesn’t just break down centralization; it rebuilds trust in code. It heralds the dawn of a decentralized, trustless internet, breaking free from the limitations and control of centralized entities. At its heart lies blockchain technology, which powers decentralized applications (DApps) and smart contracts. This gives rise to a landscape where transactions are transparent yet secure. Web3’s core promise is returning control to the users — over their data, identities, and transactions — fostering an ecosystem where trust is embedded in code and personal freedom is built into every digital interaction.
In the web3 world, old security models don’t always work well. Traditional models, like building a wall around a network, fall short because web3 is more open and decentralized. Unlike a centralized system where one entity has control, in web3, many participants across the network have a say. Old security models can’t necessarily handle this dynamic setup. For instance, DNS hijacking can wreak havoc with traditional internet platforms. Web3 aims to fix such weaknesses.
There’s a pressing need for a new security approach that’s up to the challenge, ensuring trust is earned and verified at every step. The principles of zero-trust architecture and web3’s trustless, decentralized ethos align well. Both discard the idea of implicit trust and emphasize continuous verification.
In ZTA, trust is never assumed, and every request is verified, akin to how web3 operates on consensus mechanisms where multiple nodes validate transactions. Nodes will only come to a consensus on a transaction if it conforms to the network’s rules. This shared spirit of “never trust, always verify” creates a robust framework for security and cooperation. It makes ZTA a fitting security model for web3’s decentralized landscape, ensuring only validated interactions occur within the network.
Smart contracts: Secure safeguards
Smart contracts in web3 can act as policy enforcement points, automating trust verification on each transaction. These self-executing contracts with the terms directly written into code do not run unless specified conditions are met. This innovation removes the need for intermediaries, thus accelerating transactions while enhancing security and transparency. For example, when using a smart-contract-powered decentralized exchange (DEX), users can exchange cryptocurrency tokens directly with one another without needing to trust any intermediary like a centralized exchange. DEXs provide a perfect case study of how zero-trust architecture is embedded into web3 platforms.
Identity verification
● Users access their wallets using cryptographic keys. A public key, like an address, and a private key, known only to the user, are used together for transactions.
● When a user initiates a transaction, the system uses their private key to authenticate their identity. Only the rightful owner of the private key can initiate transactions for the corresponding public key (wallet address).
Transaction authorization
● Once a user decides to make a trade on the DEX, a transaction is created. This transaction is digitally signed with the user’s private key, serving as cryptographic proof of the user’s intent and authorization.
● The transaction details and the digital signature are broadcast to the network for verification.
Continuous verification
● The blockchain network’s nodes independently verify the transaction’s authenticity by checking the digital signature using the user’s public key. This process ensures that the rightful owner of the wallet indeed authorized the transaction.
● Finally, the network verifies the conditions of the trade, ensuring that the users have sufficient balances and the trade conditions are met before executing the trade.
Permission control
● The smart contracts on the DEX enforce permission control by ensuring that only authorized transactions are processed. For instance, a user can’t spend tokens they don’t own and can’t access other user’s funds.
Cryptographic cornerstones
Throughout this process, cryptographic authentication validates identities and permissions at every step. It acts as a gatekeeper that upholds the decentralized exchange’s integrity and the trustless nature of transactions.
The foundation is laid by the SHA-256 encryption, which ensures data integrity through its unique characteristic of producing a vastly different output with a minor change in input. This encryption solidifies the first layer of trust, where the immutability of data on the blockchain is not a matter of trust but a product of cryptographic certainty. Building upon this, the Elliptic Curve Digital Signature Algorithm (ECDSA) comes into play, generating unique cryptographic key pairs for every participant on the blockchain.
Going up a level, the focus shifts to consensus mechanisms like proof-of-work (PoW) or proof-of-stake (PoS), which leverage cryptographic algorithms to achieve network agreement on the blockchain’s state. These mechanisms ensure that every transaction and block is verified by multiple network participants, embodying the zero-trust ethos of mutual verification and agreement without a centralized authority. From basic encryption to consensus mechanisms, this layered cryptographic structure meticulously builds a zero-trust environment emphasizing verification over assumption.
From fiefdoms to freedom
The relationship between zero-trust architecture and web3 embodies a concerted effort towards a secure, user-centric digital ecosystem. As they evolve together, the fundamental integration of ZTA within web3 not only addresses present-day security challenges but also fortifies the infrastructure against future threats.
Let’s end this abstract discussion of cybersecurity architecture with a historical parallel. In medieval times, as threats and raids became prevalent, cities erected walls and fortifications to safeguard their citizens and resources. The walls represented a perimeter-based security model, where trust was granted to anyone within the walls, and outsiders were viewed with suspicion.
However, as cities grew and trade flourished, these walled barriers became restrictive. The emergence of a more complex societal structure necessitated more nuanced, adaptable security measures, like passports, internal law enforcement agencies, and universal codes of law. Similarly, the shift from a walled-garden approach of web2 to the decentralized, trustless paradigm of Web3 mirrors this evolution. Just as medieval cities transitioned to more sophisticated forms of governance and security, the internet is evolving from a perimeter-based to an entity-based security model. The end result is a freer, fairer, and more inclusive internet for everyone. In this new paradigm, there’s no need to trust when you can verify.
Frequently asked questions
What is zero-trust architecture in cybersecurity?
What are the differences between web2 and web3 in terms of trust architecture?
How do smart contracts contribute to zero-trust architecture in web3?
How do consensus mechanisms ensure zero-trust in blockchain?
How does zero-trust architecture promote user-centric digital ecosystems?
About the author

Jesse Leclere is a blockchain analyst at CertiK. He combines a background in advertising with years of crypto experience and blockchain security at CertiK. Jesse has authored thought leadership pieces, detailed security reports, and incident analyses for CertiK as well as prominent external media outlets.
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.