RWA tokenization is a process of creating a digital representation of a real-world asset in the form of a token on a blockchain. This token can be traded on a blockchain network, and the ownership of the token then represents the ownership of the underlying real-world asset. This article will provide an overview of the security concerns of building an end-to-end RWA ecosystem and current industry efforts to address them.
- Desired security property: End-to-end trust path for RWA tokenization
- RWA tokenization: Bridging trust gaps in digital transactions
- Technologies that may bridge the trust gap
- Interim solution: Institutional trust
- Navigating gold tokenization
- What happens if trust breaks?
- Frequently asked questions
- About the author
Desired security property: End-to-end trust path for RWA tokenization
One of the most fundamental intrinsic values of blockchain tokens (including cryptocurrencies) comes from security. Security flaws in blockchain ecosystems can quickly devalue tokens. Hence, RWA tokenization ideally needs an end-to-end trust path between the real world and the blockchain.
Informally, this ensures that users of RWA tokens face no effective attacks in every step of the RWA tokenization process across all use cases. This applies whether they’re selling, buying, or trading RWA tokens. However, achieving this seemingly obvious security property isn’t trivial in modern computing systems, especially when these systems interact with the real world.
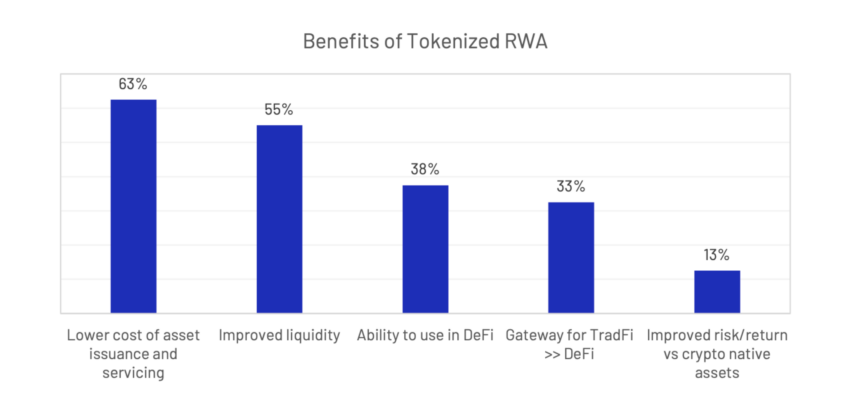
To give you an idea:
One example illustrating the challenge of achieving end-to-end trust paths is establishing trust between commodity computing systems and human beings. For instance, how can a user ensure that a malicious operating system hasn’t tampered with a computer’s screen? Surprisingly to many, securing the final step of the trust path often requires rare secure hardware and high-assurance software not commonly found in standard computing systems.
RWA tokenization: Bridging trust gaps in digital transactions

RWA tokenization processes particularly involve multiple parties. These parties include the issuer of the RWA token, the custodian of the underlying real-world assets, and the users of the RWA tokens. In almost all interactions among them, a trust gap arises between computing and the real world. In some cases, this gap is even more pronounced in human interactions.
The security of the RWA tokenization process is pivotal, just like in any other computing system. Its strength is only as robust as the weakest link among the parties and their interactions.
Some questions to bear in mind:
- How do you assure the integrity of real-world assets when the desired property is achieved via strong cryptographic primitives in blockchains?
- How can a user be assured that the RWA token he/she is buying is backed by an authentic, real-world asset, not a counterfeit?
Technologies that may bridge the trust gap
Luckily, a few candidate technologies exist that may bridge the trust gap between computing and the real world. Perhaps the most cited solution is to build an oracle between computing and the real world. An oracle acts as a trusted party that can attest to the integrity of the real-world asset on the blockchain.
In essence, the entire operation of RWA tokenization now hinges on the trustworthiness of the oracle. However, trust in blockchains is a liability we want to minimize. Trusting an oracle renders the whole RWA tokenization process vulnerable to attacks targeting the oracle.
TEE: Refining oracle security in blockchains
One expression captures this concept well: the oracle becomes a part of the Trusted Computing Base (TCB). This is integral to the RWA tokenization process.
One way to reduce the TCB regarding blockchain oracles is to use Trusted Execution Environment (TEE)-based oracles. TEE provides a secure execution environment that isolates software from the rest of the computing system.
Often, hardware implements TEEs, making it challenging for attackers to compromise the software running inside them. With hardware-based TEEs, we reduce the TCB to the hardware and the Oracle software running on the TEE, not the entire computing stacks of the Oracle system.
Approaches to real-object authentication:
Additionally, emerging efforts leverage real-world object authenticity to bridge the trust gap. There are two approaches to this. One is to measure the intrinsic properties of real-world objects and use them for their authentication. For example, wines or whiskeys have consistent intrinsic properties for each brand and product. These physical properties, such as viscosity, density, or chemical composition, can be measured in a non-invasive manner and used to test the authenticity of these assets in the real world, As shown in one Massachusetts Institute of Technology study, “Food and Liquid Sensing in Practical Environments using RFIDs,” and published by NSDI’20.
The other approach is to inscribe a unique key in the real-world objects and use it to authenticate them. Writing unmodifiable keys into real-world objects has been studied recently. Research published in 2018 has shown, for example, that it becomes difficult to counterfeit objects when digital patterns (e.g., QR codes) are written as tiny 3D objects into real-world objects through a special micro-3D printing process.
Interim solution: Institutional trust
While the technologies mentioned above show promise, they remain in their infancy and aren’t ready for large-scale real-world deployment. Therefore, in the meantime, we need to rely on institutional trust to build an end-to-end trust path for RWA tokenization. Many RWA tokenization projects currently rely on institutional trust to bridge the trust gap between blockchain and the real world.
For an RWA project to rely on institutional trust, three criteria must be met: the institution must be trustworthy throughout the trust path, each step must be rigorously evaluated for security flaws, and stakeholders and users must be informed of their reliance on institutional trust.
Navigating gold tokenization
Consider the newly introduced gold-pegged Coin ($GPC) on the Klaytn blockchain as an example. This gold tokenization initiative uses the Korea Gold Exchange, one of Asia’s leading gold exchanges, to back its tokenized gold. The tokenization process was designed to be executed in a trustless manner via smart contracts audited by reputable web3 security firms, which gives confidence for the second criterion. While it has been well-communicated so far, the project team must keep stakeholders and users informed, such as regular publishing asset audits.
What happens if trust breaks?
If institutional trust breaks at any point, it can result in a security gap between user perception and reality, potentially leading to a significant failure in RWA projects. However, traditional institutions aren’t the sole trust bridge. For example, Elysia, a multi-chain real estate tokenization platform on Ethereum, BSC, and Klaytn, uses a DAO for decentralized governance, adding a trust layer to their process. While we rely on institutional trust as a temporary solution awaiting tech advancements, it remains effective, provided the institutions’ trustworthiness for a secure RWA ecosystem is consistently monitored and upheld
Frequently asked questions
What is the security end-game for tokenized RWAs?
What upcoming technologies will help bridge the RWA trust gap?
What is the best interim security and trust solution for RWAs?
About the author
Min Suk is an Associate Professor at the School of Computing at KAIST. Before joining KAIST in 2020, Min Suk had been an Assistant Professor in the Computer Science Department, School of Computing at the National University of Singapore since 2016.
His research interests lie in the field of network and distributed systems security, blockchain security, and wireless network security. He obtained his Ph.D. degree in Electrical and Computer Engineering from Carnegie Mellon University in 2016 under the supervision of Virgil D. Gligor in CyLab. Additionally, since April 2023, Min Suk has served as an Outside Director at the Klaytn Foundation.
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




