The cryptocurrency market has been the target of several kinds of attacks over the years, with malicious actors growing increasingly sophisticated with their methods. One comparatively novel method is the crypto dusting attack, which involves sending tiny amounts to sometimes hundreds of thousands of wallets.
The attacker does not always have the intention of stealing funds, as we shall see. As far as attacks go, it is not the worst one when it comes to financial consequences, but it does have other implications.
Here we cover what a dusting attack is, why it is carried out, and any concerns you should have about it.
If you are interested in discussing this topic further, head over to BeInCrypto Trading Community on Telegram with like-minded people. Here you can share your experience, discuss and read all of the hottest news on crypto, Web3 and the Metaverse. Come Join us.
What is a dusting attack?

A dusting attack is when an attacker sends tiny amounts of cryptocurrency to bitcoin or crypto wallets. The attack does not attempt to steal the funds in any way. Rather, it focuses on using these transactions to identify the individuals or groups behind the wallets. It attempts to deanonymize users and break their privacy.
The name dust comes from these small amounts of crypto — like dust scattered across blockchain networks. You also tend to get this small amount with trades, but those are just the result of a trade, not an attack.
Dusting attacks can happen on any public blockchain, including Bitcoin.
In Bitcoin’s case, that amount would be 1 satoshi which is 0.00000001 BTC.
Many exchanges also have the option to convert these tiny amounts of crypto, usually called convert crypto dust or something to that effect.
While it isn’t as consequential as other kinds of attacks, dusting attacks have become prominent enough that it’s worth watching out for it. It’s a different kind of attack — not your usual smart contract exploitation sort of breach. But how exactly does a dusting attack work?
How does dusting attacks work?
The malicious actor would execute a dusting attack by sending dust to numerous addresses, intending to track the target addresses.
The attackers know that most cryptocurrency users don’t really notice small changes in their balances, so they monitor the outflow of these trace amounts whenever it occurs. They then use social engineering to try to discover the individual’s identity — and then blackmail them, possibly. That is the true threat of the dusting attack.
But it is what follows that could prove to be harmful. The trace amounts sent can help attackers monitor the activity of a particular wallet. Then, they use it in phishing attacks. This seems to be the intended purpose of a crypto dusting attack.
UTXO and change addresses
The UTXO based crypto assets are particularly susceptible to dusting, this is because of change addresses. Blockchains like: BTC, LTC, DASH, DCR, BCH, BTG, DGB and BSV each utilize multiple change addresses that are managed by your wallet.
Each new transaction generates a new change address to which “change” is sent. As a result, the change from your purchases never returns to the original Receive address, but instead remains in your wallet and under your control.
It is presumed that all spending addresses (the addresses on the sender side) belong to the same individual because it is uncommon for spending addresses to belong to various parties, thus they are linked to a single owner.
By sending very small amounts to multiple addresses, the dusting principle takes advantage of the mechanism of spending from multiple addresses. The attackers then trace the origins of the funds from the dust transaction and combine the affected addresses into a single identity.
Crypto dusting attack use cases
Dusting can be used for reasons other than red-hat activities. This technique is frequently used by state authorities that want to link a person or organization to an address. Governments may utilize dusting to identify terrorist cells, money launderers, criminal gangs, and tax evaders.
Furthermore, blockchain analysis firms may employ dusting to ensure regulatory compliance and safety. Developers will also use this method to conduct stress tests of their software. However, perhaps the most popular use of dusting is for advertising. Because promotional messages accompany the transactions in this case, dust is used instead of a mailshot.
Past instances of dusting attacks

One of the most notable attempts at a dusting attack occurred in 2019, when an attack saw hundreds of thousands of these dust transactions made on the Litecoin network. Later, the source of the attack was quickly identified as a group that was advertising their Litecoin mining pool. No harm was caused, but it became apparent that this could serve a malicious purpose.
Bitcoin also experienced a dusting attack in 2018. Thousands of wallets received 888 satoshi. It was later discovered to be from BestMixed, a crypto mixer platform that, again, was advertising its platform.
Another instance of dusting is when accounts on Ethereum were blocked from using DeFi apps (at least on the front end), as a result of receiving ETH that moved through US censored Tornado Cash. This dusting attack was meant as a DOS attack, rather than doxxing.
So far, there haven’t been any reported major consequences of dusting attacks. But then again, following up on such an attack is not easy, so it may very well be that some users have fallen prey to dusting attacks. It’s certainly something you want to avoid dismissing too easily.
These incidents drew attention to the negative consequences of dusting attacks — but there are some ways to avoid the worst of the attack. With these methods, you can prevent these attacks or at least avoid the consequences.
How can you avoid a dusting attack?
Fortunately, it’s unlikely that you’ll ever be subject to a dusting attack. You simply don’t use that crypto. You can flag these unspent transaction outputs (UTXO) on some platforms. And because many exchanges offer the convert to dust option, you can simply convert the dust. That’s it — you don’t have to worry about having your identity potentially outed through social engineering.
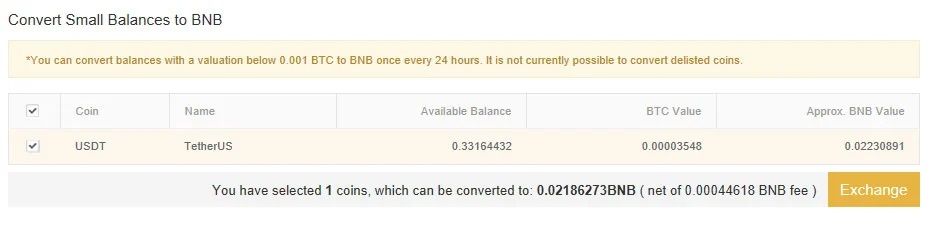
You could also use a hierarchical-deterministic wallet, which creates a new address for each transaction that you make. Of course, not all of these options are beginner-friendly, which is why it may be better to use an exchange that offers the option to convert dust.
If you take these steps, you shouldn’t have much to worry about when it comes to dusting attacks. They don’t happen so often that you have to worry about your particular address being a target. However, forewarned is forearmed.
Don’t ignore potential dusting attacks
As a unique form of attack on crypto users, dusting attacks certainly stand out. The focus on discovering the identity of the recipients is quite novel, leading to potential dangers once the dust moves. Attackers then use social engineering to begin a phishing attack, which could have more serious consequences.
More typical attacks have more serious consequences, so dusting attacks aren’t something you should be particularly vigilant about. An adversary cannot access your money with a dust attack. However, it is important to be careful in general, so if you notice a minute increase in your holdings, then don’t spend it. Better yet, make use of the convert dust option if the platform you use offers it.
< Previous In Series | Wallets
Frequently asked questions
What is a dusting attack?
How do you prevent dust attacks?
What is bitcoin dusting?
How do you get rid of crypto dust?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




