51% attacks can make blockchains vulnerable. When one party gains control of over half the network’s mining power, they can tamper with transactions or even double-spend. Understanding this risk is key to keeping your assets safe. This guide looks at the dangers of this type of attack and ways to stay safe in 2025.
KEY TAKEAWAYS
• A 51% attack allows double-spending and transaction tampering.
• PoW blockchains like Bitcoin Gold and Ethereum Classic have been victims.
• Monitoring mining power and increasing block confirmations can help prevent attacks.
51% attack explained
A 51% attack occurs when a single entity controls over 50% of a blockchain’s mining power, allowing the bad actor to alter transactions or double-spend coins. This happens because the majority control lets them decide which transactions are valid, overriding other miners.
In a blockchain, miners process transactions by solving complex mathematical problems. Each block links to the previous one, forming a secure chain. But when a party gains majority control, they can manipulate which blocks are added, making it possible to tamper with the system. This is the main risk of a 51% attack.
In a blockchain, data is stored in blocks, each linked to the previous one. Miners, or nodes, solve complex mathematical puzzles to validate transactions and add new blocks to the chain.
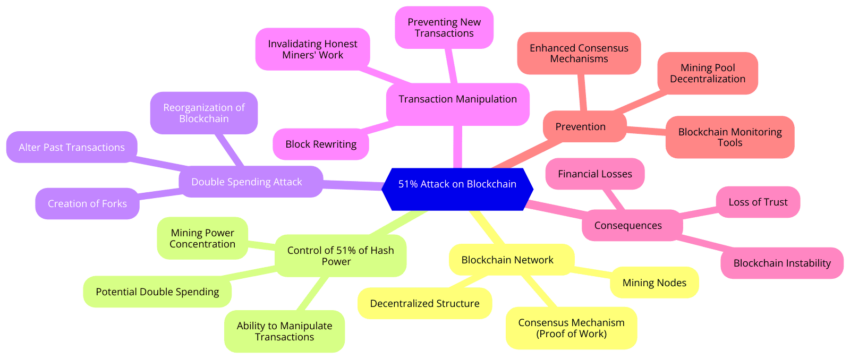
If a miner finds the solution faster than others, their block gets added. Normally, only the longest chain is valid, but when one miner controls more than half of the network, they can create a longer, alternate chain to reverse or exclude certain transactions. This undermines the security and integrity of the blockchain system.
How a 51% attack happens

When over 50% of the mining power ends up in the hands of a malicious user, they can start building their own fraudulent chain of blocks. An attacker chooses a block from a list of recently mined ones and mines an alternative chain from it. This way, a soft fork is created artificially, meaning that two equally valid chains of blocks exist simultaneously.
An attacker adds the transactions that may prove profitable into their chain. This could, for instance, be transactions that allow for double-spending. If the attacker manages to make their chain longer than the existing one, the network will accept this chain while the previous one, starting with the soft-forked block, is canceled.
This way, the attacker can spend the funds from the main chain of blocks, then replace it with the other one that contains unspent funds, and get their spent funds back. This situation sums up double spending, which is one of the primary goals of malicious users everywhere.
How bad are 51% attacks?
51% attacks can be pretty devastating. However, in a way, they get a worse reputation than what is deserved. The attack is costly: one user must have enough technical capacity to outplay all the remaining participants in the mining process.
To maintain such an attack, the user would have to create a soft fork and manage to mine the second chain of blocks, which has to be longer than the first one. That’s not an easy task by any means.
Fact check: It’s the complexity of 51% attacks that makes them less popular than flash loans or rug pulls. Note that 51% attacks only affect PoW chains and are not a threat to PoS consensus mechanisms.
Why is a 51% attack dangerous?

If a 51% attack succeeds, a malicious actor gains excessive rights. This means they have the power to cancel transactions, institute censorship over them, or stop accepting any new transactions altogether. In this case, the chain is, in a way, controlled by either one person or a group of people.
However, the most critical is the option to double-spend: to spend the same funds more than once. This kind of power over a chain is attractive to any malicious actors looking for profits.
What are some examples of successful 51% attacks?
Over the last few years, several successful 51% attacks have occurred on various chains. Among them, unfortunately, the most famous ones are present. In the past, Bitcoin Gold, Litecoin, and Ethereum have all fallen victim to this type of attack. Below we have listed so most notable examples.
Bitcoin Gold
An attack on Bitcoin Gold occurred in January 2020 and resulted in double spending of approximately $7000 worth of BTG coins. On January 23 and 24, the hard fork of Bitcoin was attacked with two reorganizations of over ten blocks. A researcher from MIT Digital Currency Initiative on GitHub reported the news.
Both attacks happened within 6 hours, with one allowing the malicious users to make $19,000 and the other adding $53,000 to this amount. The attack resulted in the coin’s price going up while Binance increased the escrow period for its purchase.
Ethereum Classic
Ethereum Classic is no stranger to majority attacks. It was hit repeatedly, especially in August 2020, three times exactly. The Bitfly mining company made it public that in three instances, 3693, 4000, and 7000 blocks were reorganized.
The last attack came right after the ETC cooperative made a statement regarding the necessity of “aggressive innovations” for the chain.
Unlike in the case of Bitcoin Gold, however, the attack didn’t have any effect on Ethereum’s coin prices.
Verge (XVG)
Verge, a privacy-focused cryptocurrency, suffered multiple 51% attacks in 2018. In April, an attacker exploited a bug in the network’s mining algorithm, gaining control and double-spending 20 million XVG (worth $1.75 million).
Despite a hard fork to address the issue, another attack occurred in May. These attacks exposed vulnerabilities in Verge’s code, highlighting the risks faced by smaller proof-of-work (PoW) blockchains.
Defense against majority attacks
While there’s no guaranteed way to prevent a 51% attack, there are measures that can help mitigate the risk. One crucial step is adjusting the number of block confirmations for a transaction to go through The more confirmations, the harder it becomes for an attacker to create a longer, fraudulent chain — this is why Binance extended its escrow period after the Bitcoin Gold attack.
Another key defense is regularly monitoring the mining process to ensure no single entity or group gains control of more than 50% of the network’s mining power. This can help identify potential risks early on.
Additional measure: Blockchain projects are also exploring hybrid consensus mechanisms (such as combining proof-of-work and proof-of-stake) to make it harder for attackers to dominate the network. These newer approaches add layers of complexity and security, making 51% attacks less feasible.
Securing against 51% attacks
When it comes to blockchain security, preemptive actions are essential. Raising awareness about the risks of 51% attacks and implementing strong defensive measures can help safeguard both users and projects.
As blockchains evolve, it’s crucial for networks to remain vigilant, monitoring mining power distribution and adopting innovations like hybrid consensus mechanisms. Ultimately, understanding and preparing for 51% attacks is one of the most effective ways to protect the integrity of a blockchain system.
Frequently asked questions
What is a 51% attack?
What are the main risks of the 51% attacks?
Are proof-of-stake (PoS) consensus blockchains vulnerable to 51% attacks?
How common are 51% attacks?
How not to become a victim of a 51% attack?
About the author
Gleb Zykov is the CTO and co-founder of HashEx. Zykov started his career as a software developer in a research institute, where he honed his technical and programming skills in the development of various robots for the Russian Ministry of Emergency Situations. He then brought his expertise to the IT services company GTC-Soft, where he designed Android applications and became the lead developer and CTO. At GTC, Gleb led the development of several vehicle monitoring services and a premium taxi service similar to Uber.
In 2017, Gleb co-founded HashEx, an international blockchain auditing and consulting company. As the CTO, he heads the development of blockchain solutions and smart-contract audits for the company’s clients.
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




