Crypto scammers can often defeat victims who do not possess basic cybersecurity education. Artificial intelligence (AI) is the solution to better security, some argue, but researchers like Jeremiah Fowler counter that human intelligence is just fine.
Companies like Cyvers.ai train AI to recognize unusual on-chain activity. Anchain.ai uses AI in its Web3SOC framework to identify smart contract vulnerabilities.
At the time of writing, there has been little to report on the success levels of these shiny new tools. In any case, they are, at best, a complement to good, old-fashioned detective work.
Just ask cyber security researcher Jeremiah Fowler.
Once a major software firm employee, the cyber expert later became the co-founder of cyber research outfit Security Discovery with fellow cyber researcher Bob Diachenko.
Since its inception, the company has made significant progress in helping people avoid crypto scams by protecting sensitive data. While the threat landscape has evolved to embrace new technologies, attack methods remain similar to bygone eras.
The key to fighting cybercrime, Fowler argues, is basic cyber hygiene. He says that educating employees on robust password management and the dangers of clicking malicious links is the first line of defense.
The same rules apply to crypto investors, who can fall victim to scams through ignorance or neglect. A seemingly endless list of software bugs that hackers can exploit adds more danger to the mix.
But there is hope for crypto investors. Read on to find out more.
One User Mistake Led to Cyber Breach at Colonial Pipeline
In the early days of banking, the biggest threat individual banks faced was the theft of cash held on-site. With the onset of new digitized systems, thieves took advantage of the relatively new cybersecurity industry to orchestrate sophisticated schemes.
While at face value, these thefts seemed very sophisticated, postmortems reveal a trail of breadcrumbs hidden in plain sight.
Take, for example, the 2021 Colonial Pipeline attack that stopped the supply of 2.5 million barrels of oil to the Eastern Seaboard. An attacker gained access through a leaked password to remotely access the plant.

An investigation revealed the password existed on the dark web. An employee likely used a password compromised from another attack to secure the connection.
User Mistakes Often Lie at Root of Most Exploits
The hack itself wasn’t sophisticated after all. It all came down to a user mistake anyone could fall victim to.

Employees can sometimes receive emails that are related to websites they’ve visited. In many cases, the familiarity of the site or certain words causes the recipient to open the email and not realize they’ve been scammed until it is too late.
According to Fowler, social engineering scams are among the hardest to stop since they are founded on a relationship between the victim and scammer. The scammer gets the victim to divulge personal or financial information after winning their trust.
But again, the attack vector is not a complicated exploit of a bug in a server somewhere. Most of the hacker’s work is carried out on the open internet, making it relatively easy to trace.
Still, that’s not to say there aren’t sophisticated actors out there.
One Weak Link Starts Infiltration at Marriott
In 2019, Marriott International CEO Arne Sorenson described a breach that compromised the guest database of their recently acquired Starwood hotel chain.
On Sept. 8, 2016, shortly after the acquisition, a database monitoring system, IBM Guardium, flagged a suspicious request to return the number of rows in the Starwood database. According to the CEO, the hacker used an administrator’s credentials to make the unusual query.
An investigation by a third party revealed hackers used malware to surveil and gain control of a computer.
Later, the forensic firm discovered a tool hackers use to probe a computer’s memory for usernames and passwords. This malware likely caused the hackers to acquire passwords, giving access to other parts of Starwood’s network.
Inevitably, the team discovered leaks of guest reservation information and a database of passport data. The breach reportedly affected the information of $500 million customers.
Complicated? Fairly.
But again, it involved the leak of one set of credentials giving access to the whole system. That was the weak point.
Public Blockchains Make Tracking Crypto Scammers Easier
Turning to crypto hacks, the public nature of blockchains largely negates the need for sophisticated tracking. In most cases, a hacker’s identity is often published as a blockchain address after major exploits.
This makes it easier for investigators to track the flow of criminal funds if the hacker doesn’t use a mixer. Even then, tracing the flows up to that point is still possible.
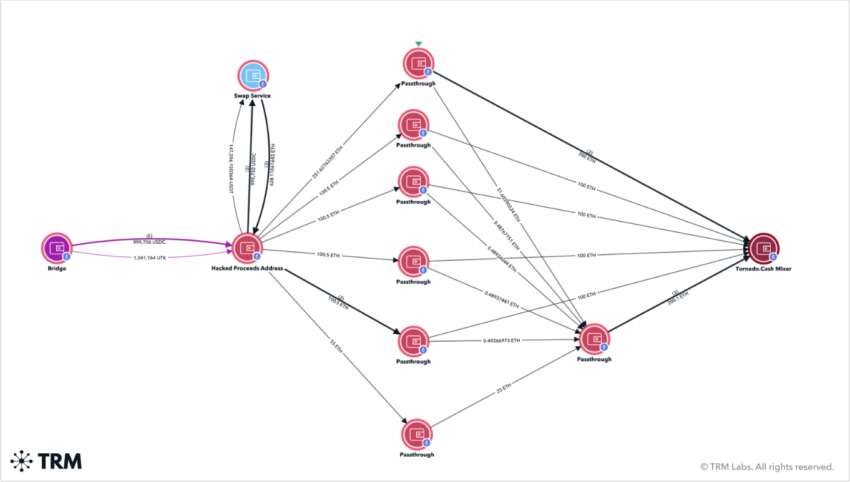
Last year, the US Treasury sanctioned a mixer accepting ERC-20 tokens to lower the risk it could be used to launder funds. The move prompted protests from Coin Center and other groups promoting censorship resistance.
Tracking Bitcoin Flows is Easy Part, Says Security Researcher
The public nature of the blockchain has made the notion of privacy a slightly moot point.
It is relatively trivial for anyone to spin up a tool to track the movement of funds on popular chains like Ethereum and Bitcoin. Anyone with a basic understanding of the process of signing transactions and how to wield a blockchain explorer can use available data to become a crypto sleuth.
Avoid becoming a victim of crypto crime. See our handy security tips here.
In fact, according to Fowler, tracking down the stolen Bitcoin is the easiest part of most investigations. While it is difficult to know a crypto scammer’s actual persona, as a cryptocurrency address masks their identities, breadcrumbs they leave in the form of email addresses, support numbers, or website assets can uncover their real identity.
“When criminals get a formula that works, they duplicate it. There is no reason to reinvent the wheel, but in the process, they get lazy and leave clues for people like me who know where to look.”
Fowler argues that the criminal can be brought to justice even if the assets cannot be retrieved. He says rather than exploring the scammer’s website through questionable means, he prefers white hat or ethical methods to determine how sophisticated their network is.
“As an ethical security researcher, I never condone or support unauthorized access of any network or website, but it is hard to feel any sympathy for criminals who target innocent crypto investors when the scammers suffer a data incident or have their network compromised.”
Bug bounties should supplement rather than replace good cyber policies. The cyber security researcher cautions against their overuse as the primary method, as many ethical researchers may turn down a low offer and leave a company vulnerable.
“In business we always say it is not if you have a data breach, it’s when you have a data breach… The latest cost of a data breach report estimates it is around $4 million but can devastate a company’s brand reputation business.”
Ultimately, companies need to be serious about protecting user data. Whatever it takes.
Got something to say about cyber security researcher Jeremiah Fowler’s methods or anything else? Write to us or join the discussion on our Telegram channel. You can also catch us on TikTok, Facebook, or X (Twitter).
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.