To many, secure access to smart contracts may seem one of the simplest elements of programming. However, it represents a crucial part of the development process. Any error or architectural choice made without regard for safety can lead to malicious actors being able to call privileged functions in contracts. Smart contract vulnerabilities will often lead to attacks, resulting in the loss of users’ funds.
Currently, there are several ways to organize access to privileged contract functions. This guide looks at the most widespread methods of reducing smart contract vulnerability.
BeInCrypto Trading Community in Telegram: get the hottest news on crypto, read technical analysis on coins & get answers to all your questions from PRO traders & experts!
How to reduce smart contract vulnerability: methods
1. Ownable contract
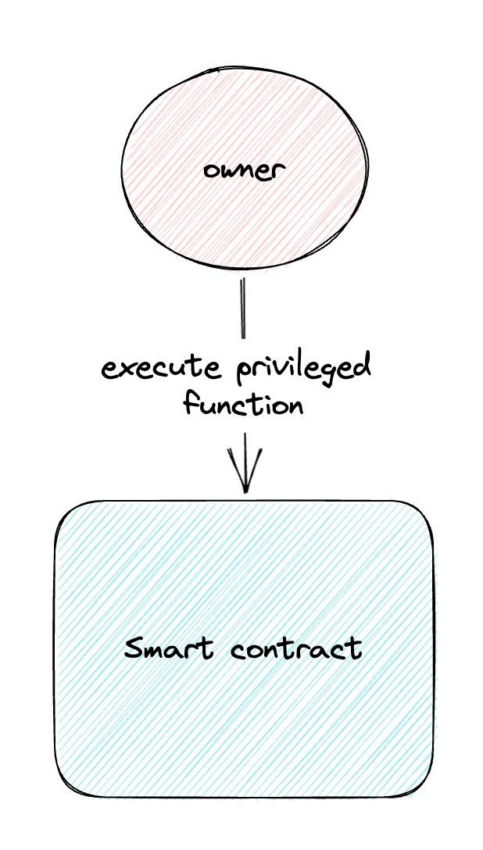
The most popular and often implemented option to organize access to smart contracts is an ownable contract. This contract implies using one address that has access to the contract’s privileged functions. These rights can be transferred to a different account or renounced altogether via a function renounce ownership.
While protecting certain functions from being called by anyone, ownable contracts present a set of disadvantages. Since there is only one address that has excessive rights, losing access to it or compromising its private key is likely to lead to dangerous consequences. Additional security is often implemented through multisig and timelock contracts, which are used alongside ownable contracts.
One account has access to all privileged functions, which increases the risks if it’s ever compromised: an attacker can receive access to all the functions at once. However, access control contracts fix this issue.
2. Access control
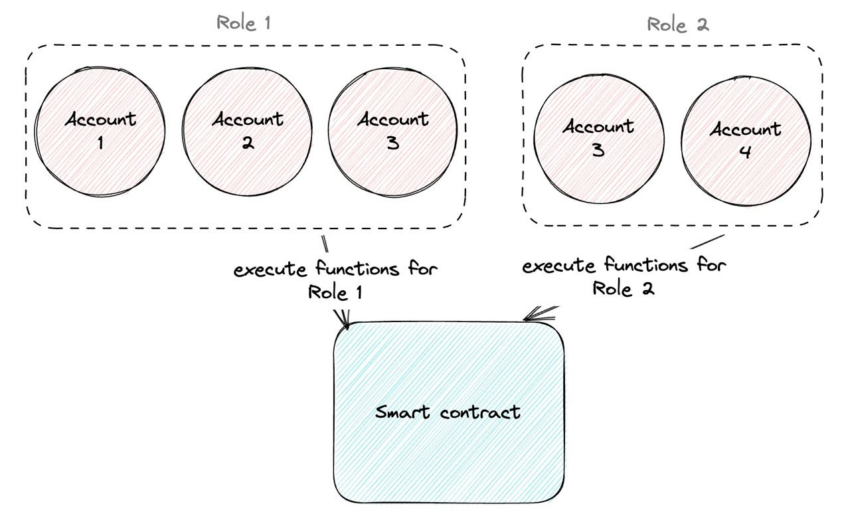
Access control presents a more complex yet flexible way to organize access to smart contracts’ privileged functions. This contract allows the set up of accounts roles, meaning specific functions can be called by assigned roles. One role can be granted to several accounts.
For instance, users with the admin role are allowed to appoint roles to other accounts.
In this sense, access control divides access to the contract; if certain functions have to be called from the backend, a specific role can be created that can call only specific functions. Meanwhile, the admin role is kept in a well-protected wallet (a cold wallet or a Multisig.)
Despite access сontrol dispersing the access, it can be implemented incorrectly. In such a case, access control runs the risk of being a less safe option than an ownable contract. For example, if an admin role is the only role used to call functions and it is given to several users at the same time. To get the most out of access control, developers have to analyze the algorithm of its implementation thoroughly.
3. Timelock
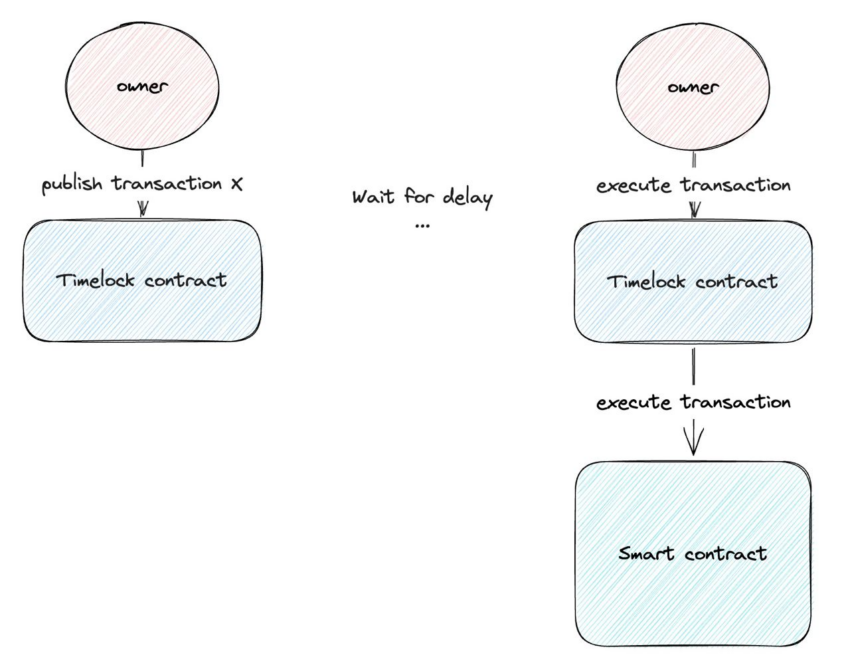
A contract that allows postponing transactions, timelock is often appointed as the owner of an ownable contract. In other words, the owner can perform any privileged functions but only after a set amount of time has passed. Before that happens, the owner has to submit the transaction into the network, which will be executed after a period set within the timelock contract.
Because an introduction of an intended transaction is a public action, users can see it and react accordingly.
A rug pull of a staking protocol serves as a vivid example. If staking is protected by a timelock, and a transaction that may remove users’ funds from the protocol is introduced to the contract, users have time to pull their funds from staking before the transaction is mined and they are taken away. Timelock adds complexity to the protocol, but fortunately, helper services with GUI have been developed to mitigate this.
4. Multisig contract
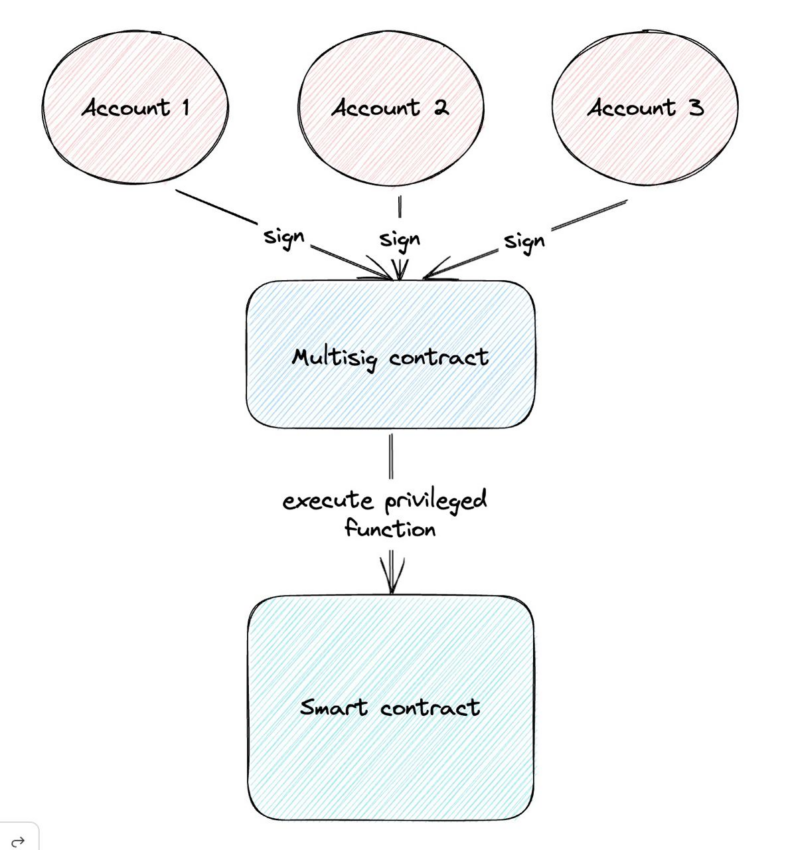
Another type of contract that can further secure smart contract access is a multisig contract. It’s also a smart contract that is often used together with an ownable one, and in this case, an ownable contract is owned by a multisig account.
A multisig allows the mining of a transaction only after it’s been signed by several accounts. Multisig wallets are flexible in their configuration. The most popular configurations are:
- 2 out of 2. The simplest form of multisig requires two accounts to sign a transaction to approve it.
- 2 out of 3. The most popular multisig configuration means that 2 out of 3 accounts need to sign a transaction before it can be mined. In this configuration, if access to one account is lost or it is compromised, the other two accounts can securely move funds to another wallet. It’s also widely used for escrow when a third-party arbitrator is needed.
- 3 out of 5. This configuration is used in bigger organizations. It provides a balance between security and convenience as it requires the majority of accounts for approval, but some accounts may be unavailable.
This process removes the risk of compromising one or even several keys, depending on its configuration, leading to inevitable losses. Multisig can be used along with both ownable and timelock contracts to achieve maximum security.
DAO
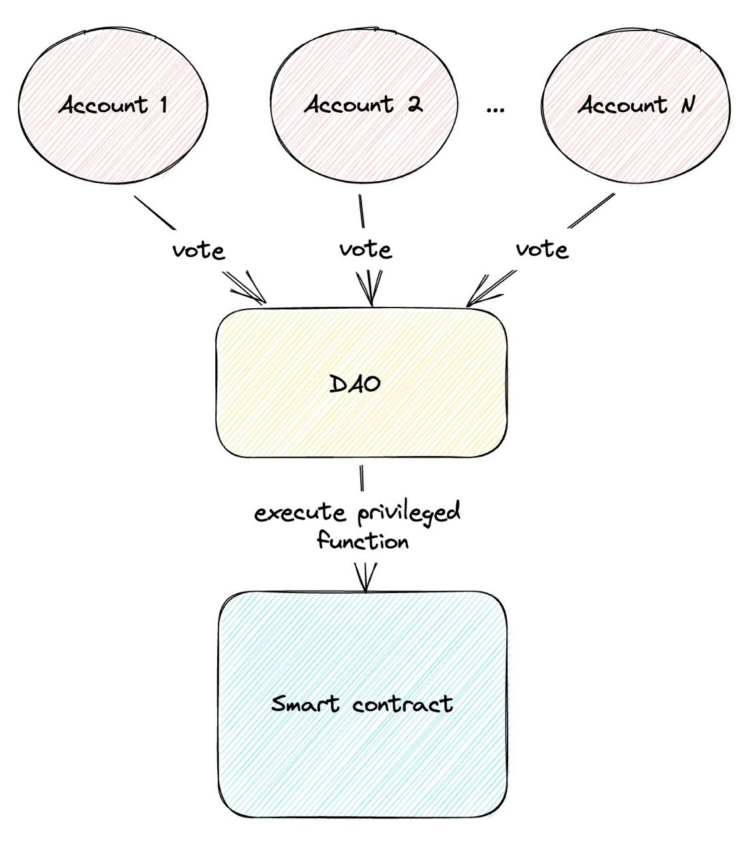
A DAO — a decentralized autonomous organization — is a system of contracts that allows control of processes through a vote. It’s the most complex of all the listed options, technically and in terms of organization. A vote is concluded with the help of tokens. And for now, this is the most decentralized way to control smart contracts and implement changes.
Yet DAO also isn’t a risk-free option. A voting mechanism can be attacked. For example, there were several infamous attacks on protocols using a DAO with flash loan attacks. A flash loan is an uncollateralized loan: a user borrows a number of tokens from a blockchain protocol, uses them, and then repays within the same transaction. In case a DAO is incorrectly implemented, an attacker can make a flash loan and vote for a malicious transaction.
Another complexity with DAOs is that organizing an honest vote with a reasonable voting power distribution isn’t an easy process. Often it’s impossible to check whether a user or a group of users are owners of several accounts that allow decisions to be made single-handedly.
It should also be noted that DAOs usually exist in a regulatory gray area, meaning they can lead to potential legal risks for participants. What if someone gets a decisive share of votes and then conducts a rug pull? Additionally, tokens used in voting may be deemed as securities by regulators, adding a layer of regulatory uncertainty to the process.
Smart contract security is vital
It’s important to know that there are tested and audited contract libraries for each one of the options mentioned above. Like cryptography, smart contracts security follows one simple rule — don’t attempt to come up with a new decision if there is a ready-made one. It is also vital to note that while we can mitigate smart contract vulnerabilities, no security option can guarantee that malicious actors won’t access privileged functions.
However, a correct implementation of access schemes and their combinations may help lower the risk of private owner keys being compromised or owners performing ill-intended actions.
Frequently asked questions
What is the best way to organize access to privileged functions in smart contracts?
What is a DAO?
Is it a good idea to implement a custom solution for access control that tailors all your needs?
About the author
Gleb Zykov is the co-founder and CTO of HashEx. Zykov started his career as a software developer in a research institute, where he honed his technical and programming skills in the development of various robots for the Russian Ministry of Emergency Situations. He then brought his expertise to the IT services company GTC-Soft, where he designed Android applications and became the lead developer and CTO. At GTC, Gleb led the development of several vehicle monitoring services and a premium taxi service similar to Uber.
In 2017, Gleb co-founded HashEx, an international blockchain auditing and consulting company. As the CTO, he heads the development of blockchain solutions and smart-contract audits for the company’s clients.
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.