As cryptocurrency grows increasingly popular, malware has been created to steal mining power from individuals, institutions, and companies through a process known as cryptojacking. Perpetrators of this new form of malware don’t steal your credentials. Instead, they secretly offload resource-intensive crypto-mining tasks to your device without your knowledge. This guide explains cryptojacking in detail, including the attackers’ methods, some real-life examples, and how you can reduce the chances of cryptojacking happening to you.
- What is Cryptojacking?
- How prevalent is cryptojacking?
- How does cryptojacking work?
- Types of cyptojacking
- Cryptojacking attack methods
- Sources of cryptojacking malware
- Cryptojacking attack examples
- How to protect yourself against cryptojacking
- How to respond to a cryptojacking attack
- Stay safe from cryptojacking
- Frequently asked questions
What is Cryptojacking?

Cryptojacking is a scheme that involves the unauthorized use of someone else’s device (computer, tablet, smartphone, or server) to mine cryptocurrencies.
Instead of spending money on crypto mining hardware, the hackers install malware onto the victim’s device to mine crypto without their consent or knowledge. By stealing computing resources, cryptojackers get an unfair advantage over legitimate Bitcoin miners without incurring costly overheads.
Unfortunately, most people don’t realize they’ve been attacked. That’s because the hackers have designed the malware used in cryptojacking to stay hidden from the victim. The vice still takes its toll as it slows down your device’s other processes, shortens the gadget’s lifespan, and increases your electricity bills. If you notice that your computer is slowing down or using its fan more than usual, there’s a chance you could be a victim of cryptojacking.
Earning quick cash is the primary motivation behind this method, especially since profiting from crypto mining is highly competitive. Therefore, cybercriminals want to mine crypto without covering the costs.
Moreover, the criminals get their targets from search engine viruses, phishing emails, social engineering, and malicious links. Unlike attacks like the 51% attack or the Vampire attack, this method is targeted at individual users, including those without knowledge or interest in cryptocurrencies.
How prevalent is cryptojacking?
Cryptojacking is one of the most common and well-hidden cyber threats in the crypto industry, having reached its climax between 2017 and 2018. The first quarter of 2018 was especially notorious, with a Fortune report indicating a 4,000 percent increase in Android-based cryptojacking incidents. During that time, hackers invaded increasingly powerful hardware, such as the infamous hijacking of a European water utility’s control systems.
At least 332 million attacks were reported in the first half of 2023, translating to a staggering 399 percent surge from 2022.
A SonicWall report observed cryptojacking perpetrators shifting their target locations in recent times. Per the report, North America experienced a 36 percent year-over-year surge, with Europe and Asia each seeing a triple-digit increase, with the former recording 6.5 times more in 2022 compared to 2021. The same report further noted that the attackers were expanding their scope beyond the Windows-based attacks and increasingly targeting Redis and Linux servers as popular targets.
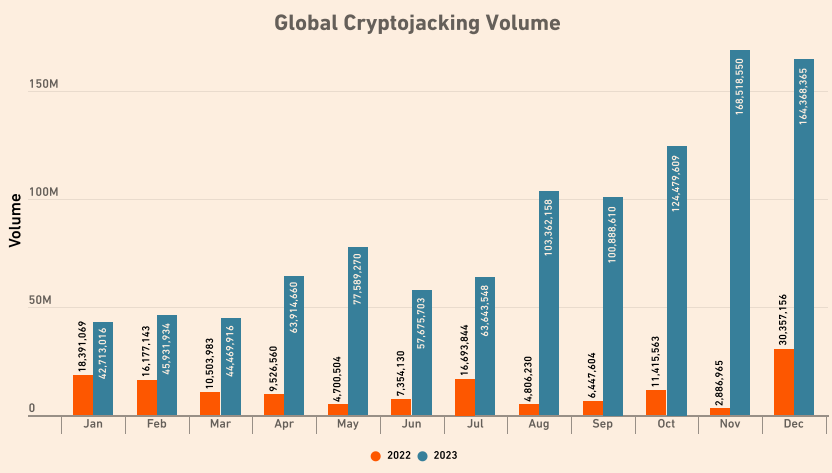
The same 2023 report attributed the rise in this type of attack to fraudsters shifting from regular ransomware to low-profile alternatives. For example, renowned hacking gang AstraLocker announced they were closing their operations to pursue cryptojacking.
Hackers are becoming increasingly innovative and daring as cryptojacking instances increase. With thousands of people using such networks across multiple devices, some universities have even been forced to shut down their networks.
How does cryptojacking work?
Cryptojacking is prevalent because it’s a stealth, low-barrier, highly profitable exercise. For instance, hackers sneak their malware script, usually some simple line of JavaScript code, into your device while browsing a website.
Once your device is infected, the crypto mining script runs undetected in the background, mining cryptocurrency, typically the anonymity-focused CPU-heavy Monero (XMR) tokens.
Hackers typically send phishing emails to victims and lure them into clicking on links or downloading malicious codes into their devices. Alternatively, cryptojackers can use cryptojacking command lines to infect websites embedded in HTML code to infect websites. Once a victim opens the infected webpage, the code gets activated, and the mining program automatically runs.
There are also types of mining malware programmed to pass the virus into a network of devices. Attackers also target vast computing resources or server farms without robust cybersecurity architecture, and the longer they remain undetected, the more cryptocurrency they mine using victims’ machines’ computing power.
Types of cyptojacking
Three primary types of cryptojacking attacks present themselves as Bitcoin miner infections, which include the following:
File-based cryptojacking
File-based cryptojacking involves downloading malware that gets executed on a victim’s device. This form of malicious crypto mining targets a victim’s computer to use its processing power to mine cryptocurrencies.
Hackers distribute malicious software using various methods, including infected attachments, malicious websites, or compromised attachments. Once the malware is activated, it installs itself on the device’s system and runs persistently, including after reboots. The infected script runs in the device’s background, increasing energy consumption while degrading performance.
Browser-based cryptojacking
This method entails inserting malicious JavaScript code into a website or an ad so it executes when an unsuspecting user accesses the compromised site. This type of cryptojacking attack relies upon a victim’s device or browser’s processing capabilities for mining. Once malware is injected, JavaScript runs inside the browser and mines crypto without the owner’s knowledge or consent. Browser-based cryptojacking can infect any computer, tablet, or smartphone accessing the infected webpage.
Cloud-based cryptojacking
Cloud-driven cryptojacking comprises an attacker illegitimately accessing cloud infrastructure and capitalizing on poorly configured security settings. The hacker then uses the cloud resources by installing mining software that capitalizes on weak security settings.
The illegal mining software employs the cloud server’s computing power in a decentralized and distributed manner. Unfortunately, it’s not easy to detect cloud-based cryptojacking since it doesn’t affect users’ devices directly, even though it still leads to higher running costs for the service provider.
Cryptojacking attack methods

There are two primary ways that hackers encroach into victims’ devices to secretly mine crypto tokens. The easiest method cryptojacking attackers use to steal a victim’s computing power is sending legitimate-looking emails to people, encouraging them to click on links. The crypto mining malware gets embedded on their device by having a victim click on a malicious code. The malicious script then runs in the background, sending results via remote control and command infrastructure.
The second method involves injecting bugs into websites or adverts delivered to multiple websites. The script automatically executes when an infected advert pops up or when a victim visits a malicious website. Hackers use these two methods individually or as a hybrid to maximize their returns.
Sources of cryptojacking malware
One of the best ways to protect your devices from cryptojacking malware risks is to know where you will likely encounter it. The most common places you can experience crypto mining bugs are in fake games and apps that activate when someone downloads them. Others have malicious websites or infected software supply chains and email attachments that users receive from unknown senders.
Hackers could also intercept and compromise authentic software suppliers to inject bugs into the supplier’s systems or applications.
Why do some miners cryptojack?
Legitimate Bitcoin mining is a lucrative way to earn BTC, and like in any other business, some miners want to generate income without incurring related expenses. Though unethical, cryptojacking enables unscrupulous miners to exploit unsuspecting victims’ resources to mine crypto. By avoiding using expensive crypto mining hardware and large electricity bills, they gain without incurring large overheads, making it attractive to cybercriminals.
Cryptojacking attack examples
The following are a few examples showing previous cryptojacking activities and their impact on the targeted companies.
Microsoft
The Microsoft Store identified eight apps in 2019 involved in malicious Bitcoin mining activities. The software manufacturer realized the resources used to mine crypto were the same, genuine ones installed by users. Microsoft finally removed the infected apps used to mine Monero (XMR), even though the damage had already been done. The JavaScript injected into the apps by the attackers was causing the targeted devices to encounter reduced and slowed-down performance.
Los Angeles Times
Media houses haven’t been spared the perils of cryptojacking, with The Los Angeles Times being a victim in 2018. The incident targeted a report page where people accessing the page had their devices infected. The bug went unnoticed for a long time, meaning the hackers used victims’ computational resources to mine a significant amount of Monero.
Coinhive
Launched in 2017 as a crypto mining service, Coinhive allowed website owners to insert a JavaScript code to enable them to mine Monero (XMR) tokens on their websites.
The plan, known as “in-browser mining,” was a form of malicious Bitcoin mining. While Coinhive had intended to provide an authentic method for website owners to make revenue from their websites without ads, attackers used it to inject cryptojacking malware into victims’ computers. Coinhive would eventually shut down in March 2019 following increased regulatory scrutiny and waning user interest.
Palo Alto Networks
The 2020 Palo Alto Networks cryptojacking occurrence involved hackers trying to attack Docker images to mine XMR. Palo Alto Networks unearthed an unlawful crypto mining scheme delivering malware to victims’ systems via Docker images on their Hub network, making a whopping $36,000. The attackers’ scheme that infected over two million images thrived because it was difficult for users to detect the presence of cryptojacking code.
How to protect yourself against cryptojacking

You only need robust crypto security measures to avoid downloading harmful software. However, users must take steps to prevent hackers from discreetly cryptojacking their devices to mine crypto.
The following security measures will help you stay safe from cryptojackers:
- Consistently update your software and devices: Any new software security updates effectively fix existing vulnerabilities by hackers always looking for loose ends in software and systems.
- Only accept software from trusted sources: Software from unlawful sources can contain crypto-mining malware that executes as soon as it’s installed. Always confirm the authenticity to ensure you’re dealing with official sources before downloading software, and check reviews.
- Stay off suspicious websites: Avoid illegal streaming sites, torrenting sites, or those that host pirated software, as they lack the security infrastructure or safety protocols you find in legitimate websites.
- Activate ad blockers in your browsers: Use ad blockers to detect and block worms appearing as pop-ups, malicious ads, and search engines containing cryptojacking scripts.
- Disable JavaScript when not in use: JavaScript is a favorite for cryptojackers who use its programming language. You can disable JavaScript whenever you are not using it to protect yourself from cryptojacking risks.
- Implement robust authentication procedures: Consider implementing strong authentication procedures, such as involving multiple ways to verify user identity before allowing users to access your systems or networks. This could help keep hackers from accessing your sensitive systems.
- Safeguard cloud resources: Secure your cloud computing services from cryptojacking by encrypting data at rest or in transit, regularly updating software, or using strong authentication.
- Employ anti-bot protection: Use software or other existing technologies to detect and stop bots, which attackers could use to distribute malware. Anti-bot protection is effective in preventing malware from reaching your computers on networks.
How to respond to a cryptojacking attack
If you’re unfortunate enough to realize you’ve become a victim of cryptojacking, you need to respond fast using the standard cyber incident response procedure. The steps include containment, eradication, and recovery.
Below are some ways to secure your devices or networks once you suspect or identify a cryptojacking attempt.
- Eradicate the malicious code: In the case of a JavaScript attack, eradicating the browser tab that ran the script is the first important step. After that, update your system’s web filters to block the infected website URL that originated the malicious script.
- Shut down infected infrastructure: In the case of a cloud-based cryptojacking attack, it’s necessary to shut down compromised containers before you can restart them. Nonetheless, it would help if you dug out the root cause to avoid a recurrence.
- Reduce permissions: Prevent the attackers from revisiting your cloud infrastructure by regenerating API keys, reducing permissions to the affected cloud resources, and installing a password manager.
- Learn and adjust: Pick up essential lessons from your experience to understand how hackers infiltrated your systems. Take up available training courses that will help you identify red flags so you can respond instantly in the future and restore your security.
Stay safe from cryptojacking
Cryptojacking is a relatively new form of elusive malware, but the number of attacks is increasing, and their nature is becoming more sophisticated. Since most users don’t notice an intrusion happening until it is too late, preventing an attack is always better than looking for a remedy. Besides looking out for red flags on sites, apps, and phishing attempts, system administrators and device owners must be proactive and install protection systems to reduce the occurrence of cryptojacking.
Frequently asked questions
What is an example of cryptojacking?
Is cryptojacking illegal?
What is the difference between ransomware and cryptojacking?
Is crypto mining Illegal?
What are cryptojacking methods?
What is a real-life example of cryptojacking?
What type of malware is cryptojacking?
How do you detect cryptojacking?
What are the dangers of cryptojacking?
Why is it called ransomware?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.