Recently, several cross-chain bridges have been frequently attacked by hackers. Crypto safety has become a hot topic of discussion, seen as the ultimate solution for enhancing interoperability between blockchains.
While DeFi allows 100% self-custody for you to control your assets, it means that you alone are responsible for keeping them safe.
On iToken Walletb, we are providing a feature called “Approval” for users that enable you to manage their permission on different chains. As whether or not you’re an experienced crypto native or a total beginner, to interact with any smart contract, you need to approve its access to your tokens.
Keys and cryptography: what is permission?
All of your crypto transactions are based on public key cryptography. Essentially, each wallet is created alone with its own private ‘key.’
Although an oversimplification, we can take the challenge of this hypothetical door and apply similar logic to your crypto wallet. Your private and public keys are both necessary to transact: the private key for you to demonstrate that you initiated the transaction, and the public key is for the recipient to verify the origin.
This process is variously referred to, somewhat unsurprisingly, as token approval. What you’re doing here is:
- To give permission to the project by allowing the smart contract to access your token balance. Think of this as the ‘smart contract stage.’ The wallet will clearly indicate at this point the value of the access that you’re giving. Some contracts/dapps may specify a finite quantity of tokens, whilst others request unlimited access.
- Confirming that you want to complete the transaction in question: Where do you allow the smart contract to submit the transaction to the network on your behalf?
How can I manage permissions?
One of the hallmarks of Web3 is providing users with full control over privacy and how they interact with its platforms.
However, it can be extended to other features as well, like the ability to view and manage dApp and smart contract approvals is amongst them.
Here’s the tutorial on iToken:
On the「Wallet」 page, choose the wallet you want to manage, and click 【Approval】 to enter the corresponding interface, on which users can see the value of the assets authorized and the value of the asset under the risk. You can cancel a token approval at any time with just one click, and we also kindly suggest you limit your authorization which keeps your asset from a high risk.
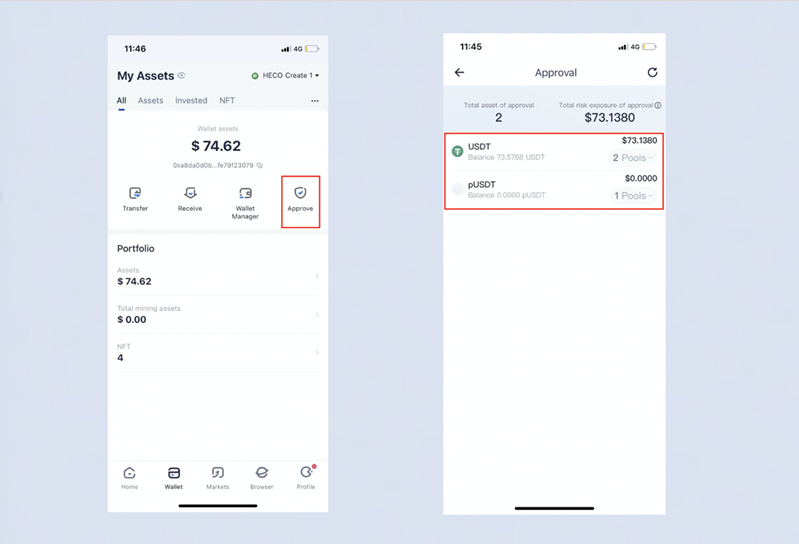
Besides that, there are some safety tips for you while keeping your asset safe.
- Improper storage of private keys and mnemonic words
If you want to use your wallet to save your assets, the easiest way is to find an unused mobile phone, download a cold wallet, and copy the wallet address within its mnemonic phrase. Don’t forget the password, but the mnemonic cannot be known to anyone. If the mnemonic or private key is leaked, the assets will be lost.
The advantage of this is that if your mobile phone is broken or you have forgotten the transfer password, there are two stored mnemonics that can be recovered. If the two mnemonics are lost, the mobile phone and transfer password are also used. However, if the phones both get lost at the same time, then it means the assets are gone.
- Entering a phishing website leads to private key leakage.
People are always excited about airdrops, but there are scammers who Use this mindset to get you to click their fake links, saying that the airdrop requires you to enter a mnemonic or private key, and then your assets disappear in a second. When using your wallet on DeFi or NFTs, please remember that the private key of the mnemonic phrase is everything. If you give this to others, you are giving money to others. No matter what type of airdrop you’re going to get, you will NEVER need the mnemonic phrase and the private key.
- The device was hacked, and the address got changed.
There’s another situation when the address is copied and pasted on your other device, like a laptop, phone or computer, etc. If your device is internet-connected, it can be hijacked and tampered with.
Therefore, when we transfer money, we must repeatedly confirm that the address is correct. Even if you transfer money by scanning the code, we must check whether the target address is correct. Often, we inadvertently relax our vigilance, the target address is tampered with, and we will just go to someone else.
During this particular period, everyone is all looking for a place to keep their assets 100% safe, and iToken Wallet is here to help you, not only just asset security but also to prevent those risks. To learn more, please download the iToken wallet here.
iToken Wallet Community:
Disclaimer
This article is sponsored content and does not represent the views or opinions of BeInCrypto. While we adhere to the Trust Project guidelines for unbiased and transparent reporting, this content is created by a third party and is intended for promotional purposes. Readers are advised to verify information independently and consult with a professional before making decisions based on this sponsored content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


