Let’s just start by calling a spade a spade — data privacy is often more of an afterthought than a priority. This is true for users who are subject to companies that enjoy unchecked access to their private personal information. Regardless, personal data protection is a digital right. Here are some tips to help you protect your digital privacy from prying eyes.
KEY TAKEAWAYS
► Data privacy ensures that your personal information shared online is used solely for its intended purpose and is protected from unauthorized access.
► Protecting personal data is important to prevent misuse, identity theft, and unauthorized access to sensitive information.
► While data protection focuses on securing data from breaches through technical measures, data privacy emphasizes who has authorized access to that data and how it’s used.
► Various countries have enacted laws to protect personal data, such as the GDPR in the European Union and the CCPA in the United States.
9 tips to protect your data privacy

Whether you are a security expert, working in the tech sector, or just someone who uses any digital device at work, home, or recreationally, you want to know these tips.
1) Password protect everything
Always password-protect each and every device you own, if possible, including your home computer, smartphone, tablet, or any other that stores your sensitive personal info. Do not make it easy for malicious actors to steal your data should you ever lose any of your devices.
It may sound obvious to some readers, but you won’t believe how many internet users still keep ridiculously simple passwords. Any password that’s even remotely guessable is a bad password. You might want to avoid that mistake.
The idea is to use a unique password for each website or online service you use. This way, even if one of your passwords is compromised somehow, the extent of the subsequent risk will be limited to only that particular website/service that you use that password for.
Granted, you probably use dozens of websites and online services regularly, like most of us do. If you worry that remembering so many unique passwords is going to be an issue sooner or later, you might consider using a trusted password manager.
2) Be extra choosy while picking a browser
Your web browser is pretty much your gateway to the web. Therefore, it makes sense to use a browser that doesn’t track your every move and offers a relatively higher degree of privacy. Brave browser, for example, promises to keep you safe from privacy-invasive ads and trackers. It blocks any third-party data storage while preventing browser fingerprinting.
Even if you are using a more popular but less privacy-friendly browser like Google Chrome, you will still want to walk that extra mile to keep your browsing habits private. The obvious first step to that would be to keep advertisers out of your browser to the extent practically possible.
The same goes for third-party cookies — you want to avoid them as much as you can. Check out these useful guides on how to block cookies in Chrome, Firefox, Safari, and Edge.
Another important precaution you can take to protect your personal data is to disable JavaScript. Doing this will deprive advertisers and potential hackers of another means of tracking you. Disabling JavaScript may affect the performance of some web pages.
3) Limit all app permissions
We have already discussed how some shady app developers stealthily gain access to your personal data through their apps. Limiting all app (or website) permissions to an absolute minimum is the only way to ensure complete personal data protection. This tip is relevant for both PCs and mobile devices.
Consider disabling all possible sources of analytics and tracking. Go through each and every app individually, if necessary, to know which apps have access to what kind of data, files, or services. Remove all unnecessary permissions. Maybe your guitar tuning app doesn’t really need to access your contacts after all!
4) Never click on suspicious links
Yeah, it may sound too obvious, but some people still make that mistake and end up compromising their online privacy. Never click on any suspicious links, pictures, banners, pop-ups, or email links that you don’t have a reason to trust.
If need be, you can use a link checker. Some malware protection applications or browsers may offer this type of protection. In fact, MetaMask offers security alerts for malicious smart contracts and decentralized applications (DApps).
5) Use social media wisely
Just because you can share every mundane detail of your life on social media doesn’t mean you have to. And even if you do, carefully consider who can access your relentless stream of status updates, memes, and photos. Even if you use social networking platforms scarcely, it is still a good idea to periodically check your privacy settings.
Additionally, some online users underestimate the power of pig butchering. In other words, you may get tons of messages from “old friends,” princes, notifications for unpaid bills, free gifts or money, job offerings, and much more. Don’t take them. Social engineering is one of the most underestimated ways attackers gain access to your information.
6) Multi-factor authentication
Another great security option is multi-factor authentication, which could cover a variety of methods. For example, passwordless authentication removes the need for a password and instead uses biometric identification—like a thumbprint or face scan—to verify credentials. It also uses cryptography, with the private key being unlocked after the verification.
You can also take advantage of authenticator apps, one-time passwords (OTP), passkeys, and sign-in with Google or other social media accounts. These methods add an additional step to the authentication process by using a device or account that only you can control.
7) Only use a secure connection
Granted, it is convenient to use the free Wi-Fi at your local Starbucks. On the flip side, however, there is no guarantee who is tracking and interpreting the internet traffic on that network. This should also go without saying that you should only use websites with an SSL/TSL certificate.
So, the rule of thumb is that if you’re on a public Wi-Fi network, avoid conveying any private information. Browsing websites is fine — specifically, websites that do not require you to enter any password or personally identifiable info. However, using online banking or entering your credit card info to buy stuff online is not.
8) Beware of phishing scams
Understand and learn how phishing scams work and how to spot one upfront. Grow familiar with how malicious actors use social engineering and other tricks to lure unsuspecting victims. Once you get to know the tricks of these con artists, it becomes way much easier to avoid them.
Using checksums is a good way to verify if you have downloaded the correct software. This is essentially a hash of the data that you are supposed to receive. If it differs from the official hash of the application, you have downloaded the wrong application, and it could steal your data or worse.
9) Setup private network
Consider connecting your home security camera and similar smart devices to a local network that transmits video or notifications only to your phone without connecting to the internet. This tip may be more advanced than the others, but it also offers high security.
Essentially, this method helps protect your data from being exposed to online vulnerabilities. Setting up a dedicated main network for your personal WiFi use and a separate guest network for visitors can add to the security of your home network and devices.
For enhanced privacy on your main network, configuring a VPN at the router level can help encrypt all outgoing traffic, securing your connected devices from external threats.
What is data privacy?

Data privacy or information privacy describes the practices meant to ensure that the data shared online by an individual is only used for its intended purpose. It is a subset of the broader data protection area that deals with the appropriate handling of user data, agreeing with existing data protection regulations.
Online privacy (also called “internet privacy” or “digital privacy”) and data privacy are widely considered among the most crucial consumer protection issues today, as they deal with the right of individuals to have control over how their personal information is collected and used.
Note that although the terms “data privacy” and “personal data protection” are sometimes used interchangeably, they’re not exactly the same. More on that below.
Data privacy vs. data protection
Simply put, data protection deals with protecting user data from unauthorized use. Data privacy, meanwhile, deals with who has authorized access to that user data.
| Data privacy | Data protection |
|---|---|
| Focuses on controlling access to personal data | Focuses on securing data from unauthorized access and breaches |
| Centers around policies and regulations | Involves technical measures and security practices |
| Concerns user consent, data collection, and data-sharing practices | Safeguards data from threats like hacking or theft |
| Attempts to ensure data is used only for agreed purposes | Aims to prevent loss, corruption, or unauthorized manipulation of data |
Data protection is mostly about having control and security infrastructure to safeguard user data. Meanwhile, data privacy requires transparency and regulatory compliance. So, in a nutshell:
- Data protection addresses technical control systems that keep data safe. Information privacy is about ensuring transparency while establishing standards and norms for data accessibility.
- The onus of ensuring data protection lies on teams consisting of experts from technical and digital security backgrounds. Information privacy teams mostly consist of experts from law and policy-making backgrounds.
- Having either of the two doesn’t automatically ensure that you have the other as well. It is possible for a company to have robust data protection mechanisms but awful information privacy standards (and vice versa).
Why is data privacy important?
To answer the question “why is data privacy important,” first, make a mental note of all the information you have shared online to date.
If you are anything like most internet users, chances are you have shared at least your name, email address, physical address, phone number, and some financial details, such as your bank account or credit card info, among others, on multiple platforms. Would you want such sensitive personal info to ever fall into the wrong hands?
Nothing good comes out of a situation that involves sensitive personal data falling into the wrong hands. For example, a data breach at a government platform could lead to enemy states or operatives gaining access to sensitive information.
A breach at a financial services provider could give away your credit card details to the perpetrators. Similarly, a breach at a university could put students’ information in the hands of malicious actors, while a breach at a healthcare facility could pave the way for potential identity theft, extortion, or insurance fraud.
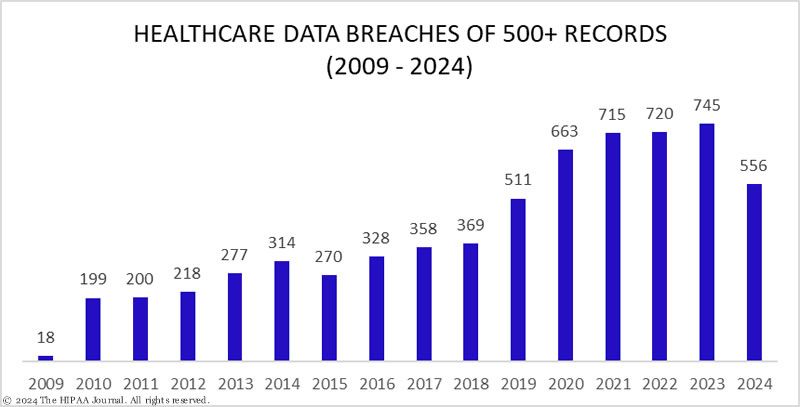
The world is becoming more digital, not less. This has led to an increase in security breaches in many sectors like healthcare, finance, crypto, and others. Personal data privacy is not merely a luxury, but a basic necessity that we cannot do without in this information age.
Data privacy laws in major economies

Most countries/regions have their own versions of data protection and privacy laws. The following is a rundown of some of these laws in major countries with substantial digital footprints:
The United States
The U.S. doesn’t have one single comprehensive data protection and privacy law that covers all types of data. Instead, it has a mix of laws, including:
Federal laws
- Fair Credit Reporting Act (FCRA): The FCRA is a U.S. Federal Government legislation that aims to ensure the accuracy, fairness, and privacy of consumer information in the files of consumer reporting agencies. It has been in effect since 1970.
- Electronic Communications Privacy Act (ECPA): Effective since 1986, the ECPA protects electronic communications data. The act covers email and telephone conversations, as well as any data stored electronically.
- Children’s Online Privacy Protection Act (COPPA): The COPPA is a federal law that imposes specific requirements on online services and website operators to safeguard the privacy of children under 13.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA mandates the creation of national standards to protect sensitive patient health information.
- Gramm-Leach-Bliley Act (GLBA): This federal law requires financial institutions to disclose how they protect and share nonpublic personal information (NPI) of customers.
- Video Privacy Protection Act (VPPA): The U.S. Congress passed the VPPA in 1988 to restrict the ability of video providers to extract and disclose a consumer’s personally identifiable information from their rental, purchase, or subscription history (of audio/visual materials).
State laws
- California Consumer Privacy Act (CCPA): The CCPA basically allows California consumers to demand access to all the information an organization, such as a company, has saved on them. The law also grants consumers the ability to see how the organization is using their personal information.
- California Privacy Rights Act (CPRA): The CPRA amends CCPA and includes additional privacy protection measures for consumers in the state. However, it doesn’t replace the CCPA.
- Virginia’s Consumer Data Protection Act (VCDPA): The law grants consumers greater control over the personal information businesses have on them. It also provides specific guidelines to businesses on how to deploy better and more practical privacy measures.
- Colorado Privacy Act (CPA): The CPA gives Colorado residents the right to opt out of targeted advertising or certain types of consumer profiling. It also prevents businesses from selling the personal data of users without their consent.
- SHIELD Act (New York): SHIELD is the acronym for Stop Hacks and Improve Electronic Data Security Act. It amends New York state’s existing data breach notification laws. Additionally, the act also imposes more stringent data security requirements on businesses that collect data on the state’s residents.
- Utah Consumer Privacy Act (UCPA): The UCPA gives Utah residents the right to 1) find out if any business is processing their data, 2) opt out from having their data processed, 3) request copies of their data, and 4) forbid a company from using their data.
European Union
General Data Protection Regulation (GDPR): GDPR is a comprehensive data protection law for regulating how companies protect EU citizens’ personal data. Some key data privacy and protection requirements of the GDPR are:
- Businesses must acquire users’ consent before processing their data.
- Data should be collected anonymously to protect users’ privacy.
- Businesses must provide data breach notifications within a reasonable time.
- Optimal safety while transferring data across borders.
- Certain businesses must appoint a data protection officer to ensure compliance with GDPR requirements.
China
China has three laws that provide a comprehensive approach to cybersecurity, data privacy, and data protection. These are:
- Cybersecurity Law (CSL): The CSL aims to protect China’s national security interests in cyberspace while combating online crime and improving information and network security.
- Data Security Law (DSL): The DSL expands on the scope of the CSL and focuses on national security, as well as the classification of data. It also expands on data localization and the cross-border transfer requirements for important data.
- Personal Information Protection Law (PIPL): Went into effect on Nov. 1, 2021. It has many similarities with the EU’s GDPR.
Top 5 major threats to online privacy

Online or internet privacy issues can range from the personal information you willingly share online and the annoyance caused by targeted ads, to targeted hacking and mass breaches. Here’s a roundup of some of the most common threats to online privacy that you should be wary of.
1) Social media data harvesting
Social media privacy issues have been frequently in the limelight for a while now. Especially after the infamous Cambridge Analytica incident that involved unethical and illegal acts, including manipulation of voters, doxing, and cyberbullying.
That was just the tip of the proverbial iceberg, though. Social media giants like Facebook (now Meta) have suffered multiple data breaches, including one that compromised the data privacy of more than 500 million users. The leaked data included the full names of users, their phone numbers, location, email addresses, and date of birth, among other details.
2) Tracking by search engines
In addition to keeping a log of your online searches, search engines also track what websites you visit. That’s not all; if your search engine provider also happens to be your browser, they can track your browsing history, too. Typically, search engines like Google and Bing collect the following types of data:
- IP address
- Search history
- Cookies
- Click-through history
They often combine this information for “profiling” you as a consumer. In other words, they use your browsing habits and preferences, online shopping preferences, and social media activities to create a consumer persona for you. Needless to say, this is a serious privacy issue.
Profiling someone with their personally identifiable information can lead to serious consequences when the data falls into the wrong hands following a cyberattack or data breach.
3) Mobile app permissions
All mobile apps require access to certain types of data and hardware to ensure optimal performance and user satisfaction. For example, it is perfectly normal for a photo editing app to request access to your phone’s gallery. Similarly, if you deny Google Maps access to your location, it will simply stop working.
However, you may have also noticed that some apps request certain permissions (or access) that do not make sense. For example, a simple app for taking text-based notes probably has no business requesting access to the phone’s gallery, camera, and microphone.
The point here is that if you are not careful, shady app developers may gain undue access to your personal data. The silver lining here is that the smartphone operating systems these days are coming with better and more practical ways to manage permissions granted to individual apps.
4) Tracking with cookies
Cookies are generally harmless and even useful. For those out of the loop, cookies are small pieces of code that collect your browsing information. Their purpose is to help websites remember your language settings, login preferences, and other details. However, cookies can be a double-edged sword if they start collecting huge volumes of data without user consent.
5) Online identity theft
As far as the history of crime goes, Identity theft has been around for a long time. In fact, it has predated the Internet for centuries. However, the information age has made it even easier for con artists to go around stealing unsuspecting victims’ identities.
Online identity theft most commonly happens when the perpetrators gain access to your personally identifiable information such as your social security number, driver’s license, bank account details, etc. In many cases, these criminals will put up your stolen identity for sale on the dark web.
The common ways to commit online identity theft include phishing, malware infection, and social engineering, among others. Personal data protection helps to avoid these types of crimes.
TikTok repeatedly proves why we need data privacy

While tech giants and social media platforms such as Google and Meta have periodically drawn flak from the authorities over their questionable approach to data privacy, TikTok seems to have taken the risk levels to a whole new level altogether.
The platform settled a class-action lawsuit in 2022 regarding the inappropriate collection and use of personal data from users. The settlement was the direct result of 21 lawsuits, including a few that were filed to protect the privacy rights of minors.
Notably, TikTok denied all the allegations but agreed to pay $92M in settlement to compensate the users affected. Note that the Indian government has already banned TikTok over security concerns. The U.S. government has not banned it yet, but the platform was under security review.
Digital privacy in crypto
2022 was the most active year for cryptocurrency hacks. Hackers stole about $3.8 billion, according to Chainalysis. However, 2021 was a close second, coming in at around $3.2 billion stolen.
Some of these hacks and exploits stemmed from smart contract failures. However, others were avoidable and a result of negligence, such as leaving one’s private keys on cloud services.
Personal data privacy is of the utmost importance in the world of cryptocurrency. Without strong data privacy protection in place, individuals risk having their personal information and financial transactions exposed to potential hackers and fraudsters, which could result in the loss of their cryptocurrency.
Personal data protection is especially important in the cryptocurrency world. This is even more relevant for figures and entities with a public face, as this likely makes them a target for exploitation. Large businesses and public faces become the object of attacks, as seen with the Wintermute exploitation.
Wintermute, a prominent crypto market maker based in the United Kingdom, lost approximately $162 million after its DeFi operations were hacked in September 2022. This hack was not caused by a smart contract vulnerability but by the use of a vulnerable private key to attack the platform, which was either leaked or brute-forced.
Cryptocurrency was created with digital privacy at the forefront, it’s what drives the innovation of the space. The proliferation of zero knowledge technology and decentralized identities shows that personal data protection is a digital right.
Always stay updated and vigilant
Ensuring and improving your data privacy is not a finite process. It requires constant vigilance as long as you use the internet. However, if you stick to these simple tips, they’ll eventually become your second habit. Also, scams and con artists are always evolving, so it makes sense to stay updated on the latest trends and events related to cybersecurity.
Frequently asked questions
What is data privacy?
Why is data privacy important?
How does blockchain support data privacy?
Is the TikTok data privacy settlement real?
How much is the payout for TikTok settlement?
How can I protect my privacy online?
Disclaimer
In line with the Trust Project guidelines, the educational content on this website is offered in good faith and for general information purposes only. BeInCrypto prioritizes providing high-quality information, taking the time to research and create informative content for readers. While partners may reward the company with commissions for placements in articles, these commissions do not influence the unbiased, honest, and helpful content creation process. Any action taken by the reader based on this information is strictly at their own risk. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.




