Google announced at its I/O 2023 conference that it would roll out new artificial intelligence (AI) tools to create content and write code that could aid crypto theft.
It will expand its AI-driven email Smart Reply email tool with newer large language models to generate messages you can refine using ChatGPT-like prompts.
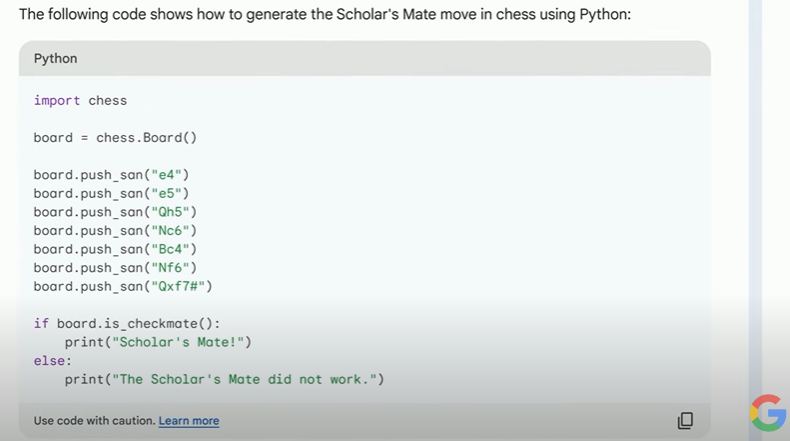
Bard Can Now Identify and Fix Software Bugs
Its PaLM 2 language model, developed by the newly formed Google DeepMind, can identify and suggest fixes to software bugs. Its ChatGPT-like conversational AI assistant, Bard, can write and interpret Python code.
A computer can execute steps in Python code in real time without understanding the whole program.
Alphabet’s CEO Sundar Pichai said the company is developing watermarking and metadata tools to identify synthetic content. Watermarking will embed certain bits of information in files in a way that will survive “modest editing.”
Users can use assess the genuineness of content through metadata offering additional context for its creation. Pichai said Google will release these tools soon.
The company reassured the public that a new video translation tool that matches lip movements with translated audio would only be used with approved partners.
As AI becomes ubiquitous, Elon Musk and other tech executives have cautioned against further training of math models. President Joe Biden has warned tech companies of the dangers of AI, with a Senate Committee announcing an AI oversight hearing next week.
How Scammers Can Steal Crypto From Smart Contracts
While tools governing responsible AI use mature, scammers can use tools like Smart Compose to elicit personal information using genuine-looking phishing emails.
These emails can be crafted to mimic the style and tenor of emails companies send to customers. Spam filters looking for poorly-crafted phishing emails may also find it harder to distinguish genuine emails from fake ones.
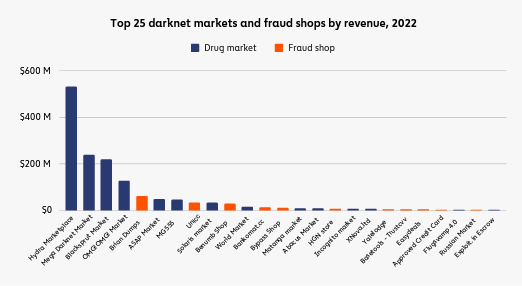
Additionally, scammers can steal personally identifiable information through malicious code Bard writes. Criminals can sell this information for crypto through fraud shops or darknet marketplaces.
Bard could also identify smart contract bugs that criminals can use to steal crypto or money. Pending tighter security measures, cross-chain bridges offer criminals a prime target. Google will roll out the assistant in over 180 countries and territories in English.
Cybersecurity firm AnChain.ai uses machine learning to analyze smart contract code for bugs.
Previously, criminals bought Google Ads leading to websites prompting customers to enter sensitive information. The scammers entice victims through urgency or lucrative opportunities and use their credentials to drain wallets on crypto exchanges.
For BeInCrypto’s latest Bitcoin (BTC) analysis, click here.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


