Victims of a recent cryptocurrency theft have filed a class-action lawsuit against financial software company Intuit Inc. for failing to secure their Mailchimp marketing product, resulting in the theft of crypto from their Trezor wallets.
The class-action lawsuit, according to Bloomberg, names financial software company Intuit and its subsidiary Rocket Science Group LLC, responsible for Mailchimp, for failing to protect its data systems adequately, resulting in one Illinois man’s loss of $87K from his Trezor wallet.
In September 2021, Intuit acquired Mailchimp $12 billion.
Recounting the Trezor phishing scam
On April 4, the Mailchimp service announced a hack affecting “audience data” from over 100 clients, including crypto wallet vendor Trezor.
Hackers used the Trezor email address to send bogus emails to Trezor clients in a social engineering attack, requesting them to click a link, disguised as a trojan horse, which looked exactly like Trezor’s app, informing the user of a “data breach” that has compromised their individual account.
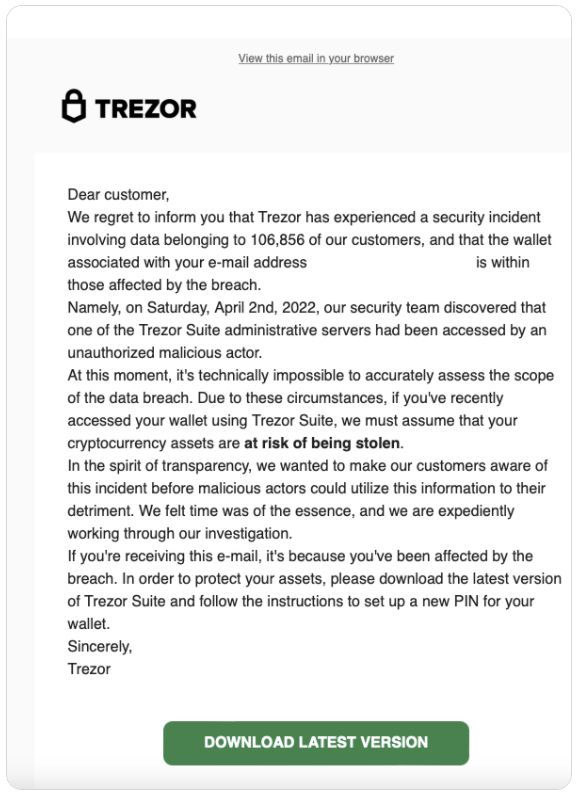
When users clicked the link, it redirected users to https://suite.trẹzor.com – rather than the legitimate www.trezor.io landing page.
The fake Trezor app exhibited features that rendered it almost indistinguishable from the genuine Trezor app. For example, unless an individual’s trained eye saw the little dot under the “e” character from trezor : “ẹ,” they would never have known. Using special Unicode characters has been a known social engineering tactic for years, and commonly associated with a Unicode domain phishing attack.
No different from most phishing cases, once the disguised link is clicked, it asks users to enter their personally identifiable information (PIAA), including user names and passwords. Trezor called the attack “exceptional in its sophistication” and indicated that it was meticulously planned.
Tool compromised, said CISO
Siobhan Smyth, Mailchimp’s chief information security officer, told The Verge that Mailchimp was informed of the breach on March 26, 2022 through a customer service and account administration tool which had been unlawfully accessed.
Sources inside Trezor told computer security news outlet Graham Cluley, that a Mailchimp insider had gone rogue and was responsible for the attack. The lawsuit also indicated that a Mailchimp employee had clicked on a phishing link.
“We sincerely apologize to our users for this incident and realize that it brings inconvenience and raises questions for our users and their customers,” Smyth stated.
“We take pride in our security culture, infrastructure, and the trust our customers place in us to safeguard their data. We’re confident in the security measures and robust processes we have in place to protect our users’ data and prevent future incidents,” he added.
For more information on the case, you can track it by following Levinson v. Intuit, Inc., 22-cv-02477.
What do you think about this subject? Write to us and tell us!
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


