A white hat hacker has returned over $7 million from the $14.5 million that was stolen in the Team Finance attack. A majority of the funds are being transferred to the affected projects.
The hacker behind the Team Finance exploit is returning funds to projects, keeping 10% as a bounty. The attack took place in late Oct., with the hacker making away with more than $14 million. The projects that were affected include Tsuka, Kondux, Caw Coin, and FEG.
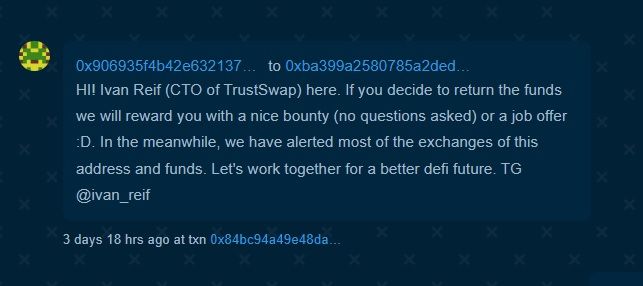
SlowMist reported that the hacker returned over $7 million to the projects. There have also been messages from the address, though they are not particularly articulate.
One interesting message came from Ivan Reif, the CTO of TrustSwap. Reif said three days ago that if the hacker returned the funds, he would be rewarded with either a nice bounty or a job offer.
It’s an interesting turn of events in the hacking incident. Occasionally, hackers return the funds and are given a bounty or a job offer. In Oct., the hacker of OlympusDAO returned all the funds in a $300 million exploit.
However, this doesn’t happen often, as hackers often prefer to keep the large amounts of funds they steal. The funds are usually funneled through a service like Tornado Cash.
Team Finance Lost $14.5 Million in White Hat Hack
The attack vector was a vulnerability in the smart contract, as the Team Finance protocol was migrating from Uniswap v2 to v3. The smart contract had been audited, but the vulnerability was missed.
The team suspended all activity on the platform, which prevented more funds from being stolen. As a result of the hack, those tokens that were stolen saw their prices drop, with CAW, in particular, seeing a large decline.
Team Finance is a platform that provides token liquidity locking and vesting services. It claims to have more than $2.6 billion in token lock value and $180 million in liquidity lock value.
Projects Using Bounties to Negotiate With Hackers
Projects appear to be increasingly interested in negotiating with hackers by offering them bounties if they return the stolen funds. This has happened on numerous occasions in 2022, most recently when the Transit Swap hacker returned 70% of the stolen funds. They received $690,000 as a bounty.
In August, crypto bridge Nomad offered the hacker of a $190 million exploit a 10% bounty to return funds. In Jan, a multichain hacker received $187,000 as a bug bounty after returning roughly $974,000 in ETH at the time.
Teams appear to be more willing to pay a bounty, but there remains a concern about the fundamental security of platforms. Protocols that have not been conducted thorough audits or have serious vulnerabilities are prime targets for hackers.
The saying prevention is better than cure is critical here and to the long-term success of the DeFi market. These bug bounties may just attract more hackers if they believe they can safely get away with some funds.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.


