In times past, wherever a nation went to war against a foreign element in the conventional sense, the engagement encompassed at least five dimensions of domain warfare. These dimensions include land, sea, air, space and information. The military conflict lasted for an undetermined duration of time, and then dissolved at the conclusion of the engagement.
However, this is not the case in the theater of cyber warfare which comprises the sixth dimension of domain warfare, where threat-actors remain persistently engaged both overtly and covertly.
North Korea’s cyber warfare capabilities are no longer questionable. According to an exhaustive report entitled “North Korean Tactics” published in July 2020 by the United States Department of the Army, “North Korea can operate across all domains and oppose U.S. interests in all phases of a joint operation.”
In North Korea, Internet access is largely restricted among its 25.55 million population, and special authorization is required in order to access it, making it fundamentally accessible by government agencies.
Nonetheless, the Army report revealed that North Korea manages 6,000 hand picked members in what is known as Bureau 121, an elite cyber warfare unit specially trained in cyber spycraft. Bureau 121 operates as a function of the Reconnaissance General Bureau of the North Korean military, the country’s premiere intelligence agency that manages the state’s clandestine operations.
Many of its members are incorporated by hackers operating from other countries such as Belarus, China, India, Malaysia, and Russia. According to North Korean defectors, Bureau 121 has a workforce of some of the most advanced computer experts.

The Subordinate Units Below Bureau 121
The following details are an outline of four subordinate units below Bureau 121, as presented in the Army report. This list isn’t comprehensive, as there are many additional threat actors (i.e. APT37, APT38, among others) at work within the realm of cyberspace for the North Korean regime, however the following are the components which make up the machinations of Bureau 121.- The Andarial Group comprises around 1,600 hackers. Their objective is to collect information by conducting reconnaissance on enemy computer systems and mapping out the network’s vulnerabilities and possible entry points within the attack vector framework.
- The Bluenoroff Group. This name was assigned to the group by cyber security company Kaspersky Lab. Its workforce is composed of around 1,700 hackers. Their modus operandi is to conduct electronic financial break-ins and earn illicit revenue on a long-term assessment for the financial gain of the regime as well as exploiting network vulnerabilities of enemy countries and institutions. Their secondary goal is obtaining military intelligence through cyberespionage, crashing networks, and intimidating those who stand in their way. Bluenoroff and the Lazarus Group are known to sometimes collaborate together on joint-operations.
- Electronic Warfare Jamming Regiment. Situated in Pyongyang, there exists a sole Korean People’s Army (KPA) electronic warfare (EW) jamming regiment which consists of three subsidiary EW battalions.
- The Lazarus Group. This group was created as early as 2007 by the government of North Korea and according to the Treasury it is a subordinate of the 110th Research Center, 3rd Bureau of the Reconnaissance General Bureau (RGB), which is North Korea’s primary intelligence service.
“Treasury is taking action against North Korean hacking groups that have been perpetrating cyber attacks to support illicit weapon and missile programs. We will continue to enforce existing U.S. and UN sanctions against North Korea and work with the international community to improve cybersecurity of financial networks.”
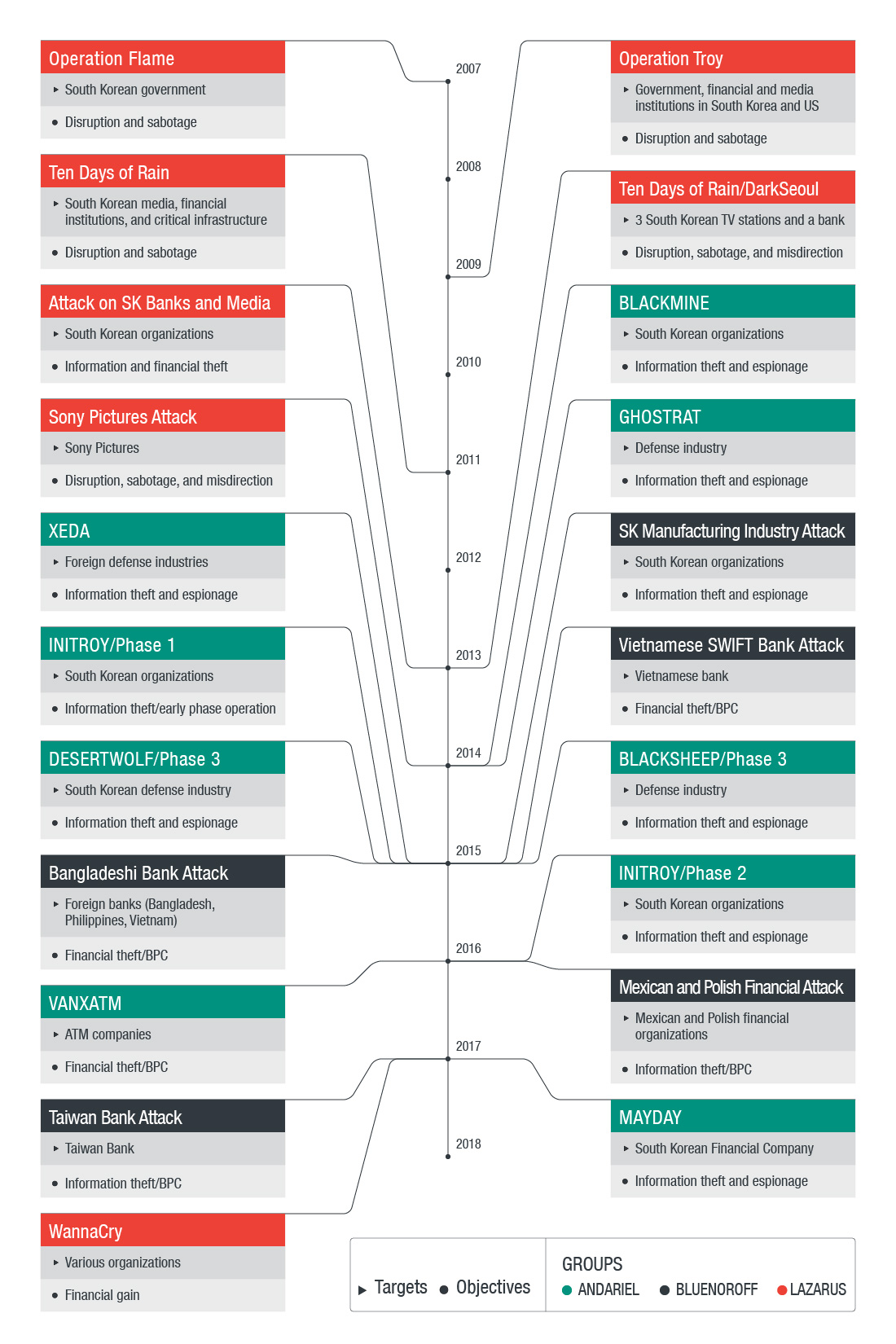
The chronology of Lazarus’s attacks. Source: TrendMicro
Hi-Tech Money Heists Fund Nuclear Expansion
While the Lazarus Group has gained much awareness in information security circles and the media, the Bluenoroff Group has quite the rap sheep of its own. As always, any hostile element that targets a country’s financial institutions with the intent to siphon off financial records and monies however physical or electronic directly impacts all individuals dependent upon that financial system. The Bluenoroff Group appeared on the radar of cybersecurity firms as early as 2014, and as time went progressed, their activities escalated. For example, in 2018 it was reported that Bluenoroff attempted to siphon off $1.1 billion dollars from foreign financial institutions. However, what was attempted in some places was actually succeeded in others. This state-sponsored hacking unit reportedly successfully carried out similar international hi-tech heists against banks located in India, Mexico, Pakistan, Philippines, South Korea, Taiwan, Turkey, Chile, and Vietnam. As with virtually all the malicious components of Bureau 121, South Korea remains a constant target and area of interest to the Korean People’s Army. According to the Army report, the ill-gotten gains procured by Bluenoroff from international financial institutions is for the financial gain of the regime. Their purpose is to accumulate stolen wealth, which then is partially utilized for proliferating North Korea’s nuclear weapons and ballistic missiles programs. In this way, the stolen monies are used to finance the KPA military’s nuclear growth while demonstrating their noncompliance in staunch opposition to the imposed U.S. sanctions.Crypto Exchanges and Financial Institutions Under Heavy Fire
Approximately 11,000 SWIFT member institutions send around 35 million transactions through the network per day. Included in the hackers’ warpath were financial institutions, and cryptocurrency exchanges. Bluenoroff is also responsible for targeting more than 16 organizations across 11 countries. They managed to break into the immense SWIFT messaging system that is used by financial institutions and banks. According to industry and press reports, Andarial, Bluenoroff, and Lazarus managed to hijack around $571 million in cryptocurrency from five different crypto exchanges in Asia between the months of January 2017 and September 2018. Dries Watteyne, the chief of customer security intelligence for SWIFT, said the attackers had intimate knowledge of how the SWIFT network processes transactions and messages between financial institutions. Watteyne stated:“They had sophisticated knowledge on a business level. They were able to make sure all messages sent from the bank and statements from the U.S. bank were hidden.”Watteyne also explained that the hackers had in-depth knowledge and understanding on how the SWIFT network processes transactions and messages between SWIFT member subscribers. Recently, Kaspersky disclosed a campaign that has been active since 2017, wherein Bluenoroff sends spearphishing emails to potential victims containing an infected archived Windows shortcut file. “The file names are disguised as security or cryptocurrency related files in order to entice users into executing them,” the report stated and further read:
“These malicious programs are responsible for stealing the user’s keystrokes and saving a screenshot of the infected machine. The main targets of this campaign are financial institutions, such as cryptocurrency businesses, and fintech companies.”According to Kaspersky, the hacker group has attacked entities in ten countries, with more potential victims from open source intelligence. Additionally, the group installed commercial cryptocurrency mining programs designed to generate Monero (XMR). However, the programs consumed such a vast amount of system resources that it disrupted the system altogether and froze completely, which prevented the attackers from being able to wipe traces of their presence from the event logs, effectively preserving the forensic evidence of the intrusion. With Bluenoroff operating as the financial crimewing of Bureau 121, cyber security firms have reported that Bluenoroff employed phishing tactics and an array of sophisticated malware attacks equipped with anti-forensic capabilities, allowing the hackers to have the ability to wipe event logs and sabotage disks. That doesn’t mean that logs were routinely cleansed by the hackers. Unused command-line based wiping tools were recovered by digital forensic experts. After the completion of a mission the hackers were to erase their digital fingerprints, however in several instances this phase of the attack appeared to be neglected for unknown reasons.
The Tactics
Kaspersky was able to identify wateringhole attacks of Bluenoroff in countries such as Poland, Uruguay, Nigeria, the Russian Federation, Mexico, India, Peru, Norway, and also Australia. Wateringhole attacks are a popular method for propagating malware used by cybercriminals. By compromising company website portals accessed by employees, the attackers were able to gain remote access to the local networks at the financial institutions they worked at simply by targeting their end users who in turn became infected, unknowingly providing an entry point for the attackers to gain access. Seongsu Park, senior security researcher at Kaspersky, weighed in regarding the attack methodology used by Bluenoroff, telling BeInCrypto:“When the Bluenoroff group attacked financial institutions, especially the cryptocurrency business, they utilized various methods to get the initial foothold into their potential victims. However, the most favorite method was spearphishing, an old technique but still a very efficient method to deliver a malicious payload to the target.”The hacker group ostensibly opted heavily for social engineering:
“Sometimes, before sending a spearphishing email, Bluenoroff would contact the victim through email or SNS message, and offer some business opportunity or ask business-related questions. After gaining trust through social engineering attacks like this, Bluenoroff eventually delivered its malware. After Blenoroff gets an initial foothold, they deliver the final payload very carefully. They collected compromised hosts’ information and delivered the next stage payload if the victim was a deemed valuable host for further attack,” Park added.A forensic analysis performed by a research partner of Kaspersky was conducted on a Command & Control (C2) server in Europe used by the Bluenoroff group. A C2 server can be understood as a computer system that is being controlled by a hacker through some sort of malicious software which enables the intruder to input commands into the infected host/network and also to retrieve information. Based on their findings, the threat actors had established a remote connection to the server by utilizing Terminal Services, commonly referred to as Remote Desktop Protocol, or RDP, and then manually installed an Apache Tomcat server from a local browser. They then configured it with Java Server Pages (JSP) before uploading the JSP script for C2. Once the server was ready to go, they proceeded with testing the setup, which began from the browser, then by performing tests to ensure that their backdoor was functioning and fully operational. They used multiple IPs, from France to Korea, and established connections by using different proxies and VPN servers. However, in the scheme of establishing their operations security (OPSEC) there was a particular instance when one short connection was established originating from a very unusual IP range, which happens to originate in none other than North Korea. This brief connection is an indication of the originating connection, linking the intrusion back to the intruders. The level of sophistication demonstrated by this state-sponsored APT isn’t typical of most criminal hacking organizations. Their level of malware coding prowess, ability to reverse engineer software and write their own patches, as well as their aptitude in security infiltration — in conjunction with knowledge of the inner workings of proprietary industry systems offers more than an allusion to the level of superior organizational skills, as well as unique training that would otherwise be necessary to develop such a formidable syndicate. Advanced Persistent Threat Actors under the control of hostile foreign powers such as seen here are indeed a threat that every financial institution apparently should take seriously in their pursuit in developing viable network security solutions if they hope to prevent intrusions being perpetrated at this level.
Top crypto platforms in the US
Disclaimer
In line with the Trust Project guidelines, this price analysis article is for informational purposes only and should not be considered financial or investment advice. BeInCrypto is committed to accurate, unbiased reporting, but market conditions are subject to change without notice. Always conduct your own research and consult with a professional before making any financial decisions. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.

Jesse McGraw
Jesse McGraw is a former classical concert pianist. He is also known by his
moniker GhostExodus, and is also the former founder of a hacktivist group.
Naturally, he is passionate about cyber security, being a former threat
actor and insider threat. Aside from InfoSec, justice reforms and other social
impact initiatives are topics important to him. But after its all said and done,
he slinks off to plays his violin and makes waffles.
Jesse McGraw is a former classical concert pianist. He is also known by his
moniker GhostExodus, and is also the former founder of a hacktivist group.
Naturally, he is passionate about cyber security, being a former threat
actor and insider threat. Aside from InfoSec, justice reforms and other social
impact initiatives are topics important to him. But after its all said and done,
he slinks off to plays his violin and makes waffles.
READ FULL BIO
Sponsored
Sponsored

