On August 7, 2025, the US Department of Justice convicted Tornado Cash co-founder Roman Storm for running an unlicensed money transmission business. The case, seen as a crackdown on crypto mixing infrastructure, directly affects hacker groups’ laundering networks.
Weeks later, on August 26, the FBI confirmed that the Lazarus Group was behind the $1.5 billion Bybit hack — the most significant theft in crypto history.
“North Korean Hacks” Stretch Across Global Markets
Why Important
The Bybit breach and the Tornado Cash verdict highlight how cybercrime and regulation collide. For investors and exchanges, this is not just about stolen assets — it is about rising compliance costs, tighter oversight, and the perception that crypto has moved from a financial risk to a national security issue.
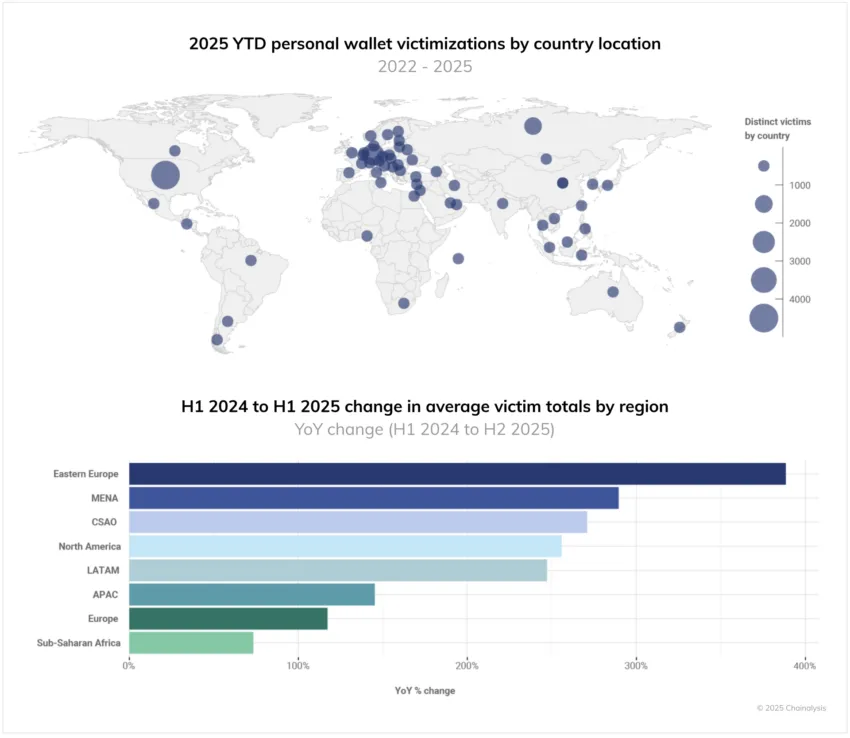
2025 YTD personal wallet victimizations by country location | Chainalysis
Latest Update
The FBI’s confirmation of the Bybit theft and the DOJ’s conviction of Tornado Cash’s co-founder mark a turning point. Authorities now pursue both the hackers and the infrastructure that launders their proceeds. Moreover, regulators signal that enforcement will broaden to cover perpetrators and enablers across the industry.
Background Context
Since 2017, the Lazarus Group, an unknown hacker group alleged to be run by the North Korean government, has targeted banks and crypto exchanges to generate funds. The narrative of its origin stems from the fact that, because international sanctions restricted trade, Pyongyang pivoted to cyber theft. By 2025, the pace accelerated, with attacks spanning Asia, the US, and Europe. At the same time, global law enforcement struggled to keep up with the speed of attacks.
A Year of Escalation
Deeper Analysis
The wave began in May, when Taiwan’s BitoPro exchange lost about $11.5 million. In June, the DOJ filed a forfeiture action to seize $7.74 million linked to laundering schemes. Later that month, four North Korean nationals were indicted in Georgia for infiltrating US firms as IT contractors, stealing nearly $900,000. Meanwhile, investigators noted this was part of a broader pattern rather than isolated cases.
A TRM Labs report estimated North Korea stole $1.6 billion in the first half of 2025, accounting for about 70 percent of global crypto crime. In June, the Financial Action Task Force warned that North Korea posed the most severe state-based threat to the integrity of crypto markets. Beyond that, regulators worldwide began reviewing licensing frameworks more aggressively.
“With over $2.17 billion stolen from cryptocurrency services so far in 2025, this year is more devastating than the entirety of 2024. The DPRK’s $1.5 billion hack of Bybit, the largest single hack in crypto history, accounts for the majority of service losses.” — Chainalysis
Hidden Tactics Exposed
Behind Scenes
A Wired investigation revealed over 1,000 email accounts linked to North Korean IT workers employed remotely by Western companies. Salaries moved into crypto wallets, then laundered through mixers and cross-chain swaps. This “dual strategy” — steady inflows from IT jobs plus windfalls from exchange hacks — provides Pyongyang with durable funding streams. Moreover, experts observed that this combination allows the regime to balance reliable income with occasional billion-dollar windfalls.
North Korean operatives have also upgraded their toolkit. As BeInCrypto reported, they now combine advanced social engineering with zero-day exploits. Consequently, their success rates rise even against platforms once considered secure.
Wider Impact
These incidents have shaken confidence in the industry. European exchanges report higher compliance costs, while South Korea has expanded blockchain forensics. The FATF warning pushed several governments to tighten licensing frameworks. Consequently, oversight has shifted from a financial lens to a security one — a change that directly impacts investors and platforms alike.
Military Diversion Risks and Policy Reactions
Essential Facts
• North Korea stole $1.6 billion in H1 2025 (TRM Labs).
• The Bybit hack alone cost $1.5 billion (FBI).
• BitoPro lost $11.5 million (Yahoo citing BitoPro).
• DOJ filed a $7.74 million forfeiture action (DOJ).
• Four nationals indicted for $900,000 thefts (DOJ).
• UN monitors reported that cyber proceeds fund weapons programs.
Looking Forward
Officials warn that Pyongyang is testing decentralized finance and privacy coins. Consequently, analysts expect new sanctions on mixers, custodial wallets, and liquidity pools. Without coordination, enforcement gaps will widen, leaving investors exposed.
Data Breakdown
| Date | Event | Amount | Source |
|---|---|---|---|
| May 9, 2025 | BitoPro hack (Taiwan) | $11.5M | Yahoo News |
| June 5, 2025 | DOJ forfeiture action | $7.74M | DOJ |
| June 30, 2025 | DOJ indictment (4 nationals) | $0.9M | DOJ |
| June 2025 | FATF warning | N/A | ICBA |
| May 2025 | IT worker scheme exposed | N/A | Wired |
| Aug 7, 2025 | Tornado Cash verdict | N/A | DOJ |
| Aug 26, 2025 | Bybit hack | $1.5B | FBI |
| H1 2025 | Global theft total | $2.17B | Chainalysis |
From Past Heists to Today’s Dominance
Between 2017 and 2022, UN panels estimated that Pyongyang, including the Lazarus Group, generated about $2 billion through cyber theft. By 2024, North Korea represented nearly one-third of global crypto crime. By 2025, its dominance expanded dramatically, driving most major heists. Moreover, the shift from opportunistic hacks to systematic campaigns shows the regime’s growing sophistication.
Possible Risks
Sanctions may tighten, but peer-to-peer transactions in emerging economies create blind spots. Consequently, DPRK will likely pivot to decentralized corridors. This implies sustained liquidity risks, higher regulatory costs, and potential sudden market restrictions for investors.
Expert Opinions
“Cybercriminal activities generate about half of North Korea’s foreign currency income and are used to fund its weapons programs.”
— UN sanctions report, June 2025
“These funds enable DPRK’s malign activities worldwide, undermining sanctions and fueling proliferation.”
— US Department of Justice
“The Lazarus Group’s strategy has evolved from opportunistic hacks to structured, state-backed funding operations, making them harder to disrupt.”
— TRM Labs analyst
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.