Last year in July, Cornell University computer science professor Emin Gün Sire tweeted about a new malware that bluffed its way into blackmailing unsuspecting victims. The perpetrators of the scheme made victims think that their taste in porn and intimate sexual moments had been secretly captured on video and the only way out was to pay a ransom in Bitcoin.
The malware was later dubbed ‘Save Yourself‘ as the recipients often got these bogus sextortion demands from email addresses containing the phrase “Save Yourself” — for example, [email protected].
Now, it turns out, the Save Yourself malware was designed to have a side-gig as well, according to the researchers at cybersecurity firm, Reason Security.

‘Save Yourself’ Eats Up Your PC’s Processing Power
The plight of the Save Yourself victim typically begins with an email notifying them that their computer has been infected by a dangerous malware. In reality, that’s not always the case — but the perpetrators take advantage of the fact that most users have no sure-shot way to call out the bluff. Even though the malware’s primary role is to force devices into serving as blackmail proxies, the researchers at Ranson Security have now found that it serves a dual purpose by acting as a crypto-mining malware. More specifically, Save Yourself smuggles an elusive program that infiltrates the host machine and secretly starts mining the privacy-focused cryptocurrency, Monero (XMR). In doing so, it might end up consuming up to 50% of the host’s CPU power, thereby adversely affecting its performance, but only to a limited extent to avoid raising suspicion. All the Monero coins thus generated are deposited in the perpetrators’ wallet(s).
Your Bitcoin At Risk
Turns out, the malware is also capable of reading data from the clipboard and timely intercept whenever a Bitcoin transaction is being made. It then executes a special module that replaces the intended recipient’s Bitcoin wallet ID with the perpetrator’s own without triggering any alarm. Apart from that, Save Yourself is also believed to be designed to compromise most types of executables on the target machine, which makes it easier for the malware to spread and auto-infect.How Dangerous Is ‘Save Yourself’?
Security researchers recommend that the recipients of the sextortion emails don’t take the perpetrator’s claims for their face value. So far the evidence suggests that the attackers most certainly can not record victims’ activities on porn websites and neither do they have the ability to activate a webcam remotely.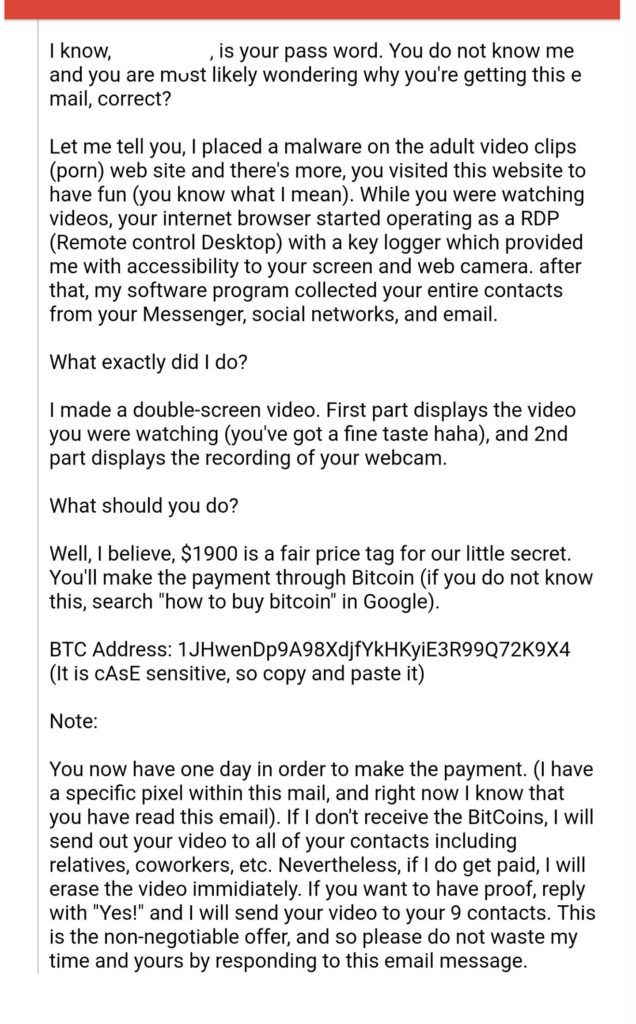 So, the best course of action, in most cases, would be to simply ignore such emails. Even if the email contains a password you have previously used (or are still using), it is probably because those credentials were exposed long back during an earlier cyberattack and are currently lying in some corner of the dark web. In such cases, all you have to do is change your passwords and activate 2FA where possible.
The real threat of the malware is on the technical front considering that it has the firepower to inflict serious damages, but only when it manages to infiltrate the target’s defense mechanism. As it turns out, most updated antivirus software can detect and neutralize the malware relatively easily.
Meanwhile, there are unconfirmed reports that the attackers have recently switched to Litecoin as their preferred mode of ransom to avoid being flagged by email filters.
Some estimates suggest over 100,000 internet users have so far been victims of the Save Yourself malware. Those of you who happened to have bumped into Save Yourself or any similar cyberattack of that nature, share your experience in the comments below.
So, the best course of action, in most cases, would be to simply ignore such emails. Even if the email contains a password you have previously used (or are still using), it is probably because those credentials were exposed long back during an earlier cyberattack and are currently lying in some corner of the dark web. In such cases, all you have to do is change your passwords and activate 2FA where possible.
The real threat of the malware is on the technical front considering that it has the firepower to inflict serious damages, but only when it manages to infiltrate the target’s defense mechanism. As it turns out, most updated antivirus software can detect and neutralize the malware relatively easily.
Meanwhile, there are unconfirmed reports that the attackers have recently switched to Litecoin as their preferred mode of ransom to avoid being flagged by email filters.
Some estimates suggest over 100,000 internet users have so far been victims of the Save Yourself malware. Those of you who happened to have bumped into Save Yourself or any similar cyberattack of that nature, share your experience in the comments below.
Top crypto platforms in the US
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.

Shilpa Lama
Shilpa is a Highly experienced freelance Crypto and tech
journalist who is deeply passionate about artificial intelligence and pro-freedom technologies such as distributed ledgers and cryptocurrencies.
She has been covering the blockchain industry since 2017. Before her ongoing stint in tech media, Shilpa was lending her skills to government-backed fintech endeavors in Bahrain and a leading US-based non-profit dedicated to supporting open-source software projects.
In her current...
Shilpa is a Highly experienced freelance Crypto and tech
journalist who is deeply passionate about artificial intelligence and pro-freedom technologies such as distributed ledgers and cryptocurrencies.
She has been covering the blockchain industry since 2017. Before her ongoing stint in tech media, Shilpa was lending her skills to government-backed fintech endeavors in Bahrain and a leading US-based non-profit dedicated to supporting open-source software projects.
In her current...
READ FULL BIO
Sponsored
Sponsored

