The United States Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), the Netherlands’ National Cyber Security Centre (NCSC-NL), and Europol’s European Cybercrime Centre (EC3) have issued a joint warning about Akira ransomware.
The group is responsible for attacks on over 250 businesses and critical infrastructure entities since March 2023, primarily in North America, Europe, and Australia.
Akira’s Evolution and Attack Techniques
Akira threat actors have amassed an estimated $42 million in ransom payments as of January 1, 2024. They have targeted various industries, raising significant concerns for organizations worldwide.
Initially written in C++, Akira originally encrypted files with a .akira extension. However, variations have emerged. Starting August 2023, the group deployed the Rust-based Megazord ransomware, adding a .powerranges extension to its encrypted files. Some attacks now involve deploying both Megazord and Akira variants for increased impact.
Read more: Top Cryptocurrency Scams in 2024
The FBI and cybersecurity researchers have traced Akira’s initial access methods. Commonly, they exploit known vulnerabilities in Cisco VPN services that lack multifactor authentication (MFA). They also gain entry through remote desktop protocols, spear phishing, and compromised credentials.
Once inside a network, Akira attackers create new domain accounts to maintain persistence. They then leverage credential scraping tools like Mimikatz to escalate privileges. System reconnaissance and the identification of domain controllers are performed using tools like SoftPerfect and Advanced IP Scanner, along with native Windows commands.
Akira actors frequently disable security software before moving laterally across compromised networks. PowerTool has been observed turning off antivirus processes to evade detection.
To steal sensitive data, Akira operators extensively use exfiltration tools like FileZilla, WinSCP, and cloud storage services. They establish command and control channels with AnyDesk, RustDesk, and Cloudflare Tunnel.
True to the double-extortion model, Akira actors encrypt systems after stealing data. Their ransom note includes a unique code and a .onion URL for contacting them. They don’t specify an initial ransom amount, pressuring victims into negotiations.
Ransom payments are paid in Bitcoin to crypto wallet addresses provided by the threat actors.
Furthermore, to apply extra pressure, Akira threat actors threaten to publish exfiltrated data on the Tor network and, in some instances, have called victimized companies, according to FBI reporting.
The FBI, CISA, EC3, and NCSC-NL have issued comprehensive recommendations for the Akira threat actors’ system and network discovery techniques. Implementing these mitigations can significantly reduce the risk of a successful attack.
“In addition to applying mitigations, the FBI, CISA, EC3, and NCSC-NL recommend exercising, testing, and validating your organization’s security program against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework in this advisory,” CISA wrote on its report.
Read more: Top 5 Flaws in Crypto Security and How To Avoid Them
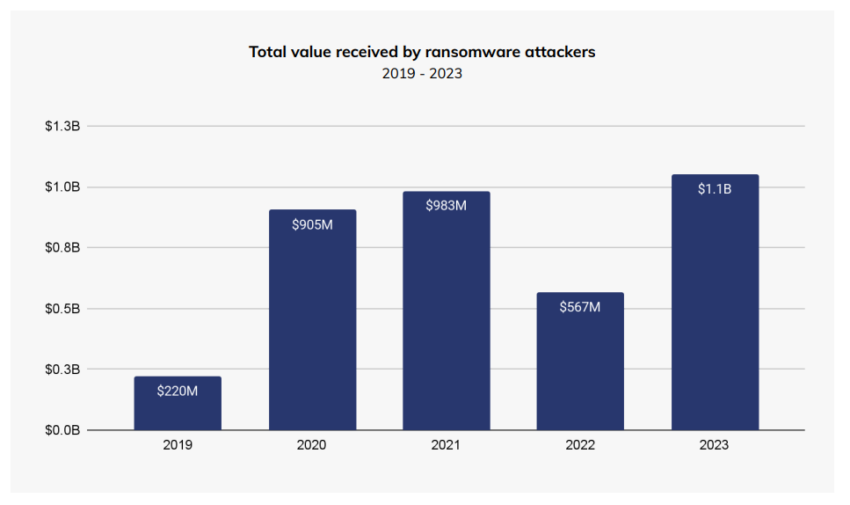
According to a February 2024 Chainalysis report, ransomware attacks intensified in 2023, with $1 billion extorted from victims. This highlights the growing cyber threat and the need for organizations to enhance their cyber defenses.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.



