Researchers on Thursday discovered a new trojan targeting crypto traders using Mac’s.
Researchers from internet security firm ESET, found that legitimate-looking websites are distributing malicious cryptocurrency trading applications for Mac users. Dubbed GMERS, the malware could “steal information from browser cookies, crypto wallets and screen captures,” a release said.
According to researchers, the malware authors used the original website of the Kattana crypto trading terminal to re-brand their own spying applications. The researchers also created fake honeypots to reveal the real intentions of the criminals.
“We have seen the following fictitious brandings used in different campaigns: Cointrazer, Cupatrade, Licatrade and Trezarus,”the analysts said. Kattana had raised a warning in March, stating that perpetrators had lured traders individually to download the trojan application. The trading platform said users should be “extra mindful” of such fraudsters.
Researchers were unable to connect this campaign to the current GMERS malware.We’ve come to know that some of our users were approached by the malicious copycat service of Kattana, located at: https://t.co/paSARVJPPZ
— Kattana (@kattanatrade) March 12, 2020
Please, be extra mindful about anyone who approaches you for any reason related to crypto-trading. They might be frauds.
“We have not yet been able to find exactly where these trojanized applications are promoted,”they added.
Copycat Websites Look Legitimate
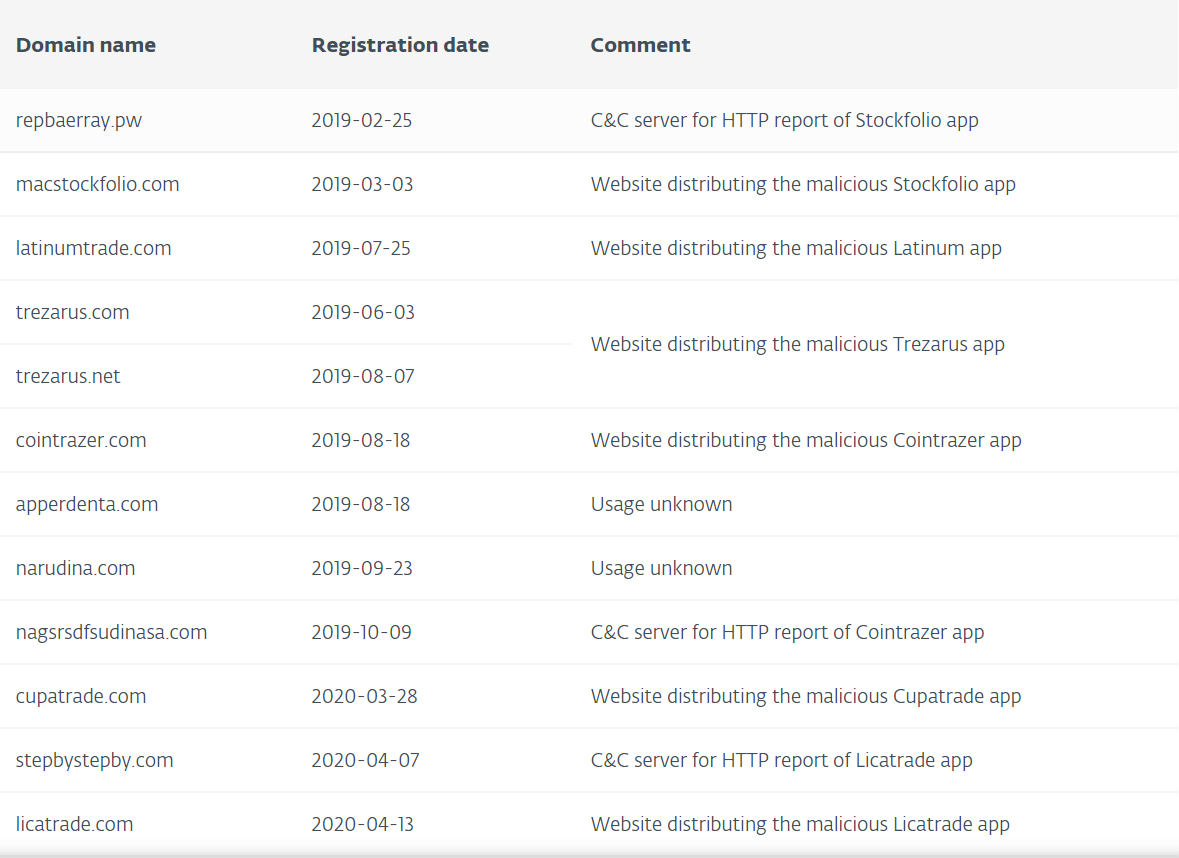
The perpetrators are duplicating websites to make the bogus application download look legitimate. Researchers wrote, “for a person who doesn’t know Kattana, the websites do look legitimate.” The download link then takes users to a ZIP archive containing the fake application bundle. Kattana requires user credentials for trades on its platform. Researchers also examined these to prevent login thefts. They noted:“We wanted to see if, besides the change in name and icon in the application, some other code was changed.”The Licatrade application, for example, had a malicious app on its original-looking licatrade.com website. Malware authors used the same email address to register this and several other domains, analysts noted. Here are a few of the copycat domains registered with same email addresses, revealing previous malicious campaigns:
Setting up Crypto Honeypots
In order to monitor all interactions between malware operators, researchers set up fake honeypots, a computer security mechanism. These honeypots can detect or deflect unauthorized use of information systems by fooling cybercriminals into thinking they’re legitimate targets. For example, the honeypots can mimic a company’s customer billing system to attract fraudsters. This looks like a real computer system for hackers. Once criminals ‘access’ the honeypots, they are tracked and assessed. Analysts said that the perpetrator’s interest lies primarily in cryptocurrency wallets, screen captures, and browser information containing user history and cookies. They said, that the attackers were directly contacting victims and “socially engineering them” to download the malicious application.Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.
Sujha Sundararajan
Sujha reports on cryptocurrencies, blockchain developments and markets, operating from the South East Asia timezone. Her work has appeared in CoinDesk, CCN, EconoTimes and Venture Capital Post. She does not currently hold value in any digital currencies.
[email protected]
Sujha reports on cryptocurrencies, blockchain developments and markets, operating from the South East Asia timezone. Her work has appeared in CoinDesk, CCN, EconoTimes and Venture Capital Post. She does not currently hold value in any digital currencies.
[email protected]
READ FULL BIO
Sponsored
Sponsored
